How to Secure Regulated Data in Microsoft 365 Copilot
Microsoft 365 Copilot is a game-changer, embedding generative AI directly into your favorite tools like Word, Outlook, and Teams, and giving productivity a huge boost. But for governance, risk, and compliance (GRC) officers and CISOs, this exciting new innovation also brings new questions about governing sensitive data.
So, how can your organization truly harness Copilot safely without risking compliance? What are Microsoft 365 Copilot security best practices?
Frameworks like NIST’s AI Risk Management and the EU AI Act offer broad guidance, but they don't prescribe exact controls. At Sentra, we recommend a practical approach: treat Copilot as a sensitive data store capable of serving up data (including highly sensitive, regulated information).
This means applying rigorous data security measures to maintain compliance. Specifically, you'll need to know precisely what data Copilot can access, secure it, clearly map access, and continuously monitor your overall data security posture.
We tackle Copilot security through two critical DSPM concepts: Sanitization and Governance.
1. Sanitization: Minimize Unnecessary Data Exposure
Think of Copilot as an incredibly powerful search engine. It can potentially surface sensitive data hidden across countless repositories. To prevent unintended leaks, your crucial first step is to minimize the amount of sensitive data Copilot can access.
Address Shadow Data and Oversharing
It's common for organizations to have sensitive data lurking in overlooked locations or within overshared files. Copilot's incredible search capabilities can suddenly bring these vulnerabilities to light. Imagine a confidential HR spreadsheet, accidentally shared too broadly, now easily summarized by Copilot for anyone who asks.
The solution? Conduct thorough data housekeeping. This means identifying, archiving, or deleting redundant, outdated, or improperly shared information. Crucially, enforce least privilege access by actively auditing and tightening permissions – ensuring only essential identities have access to sensitive content.
How Sentra Helps
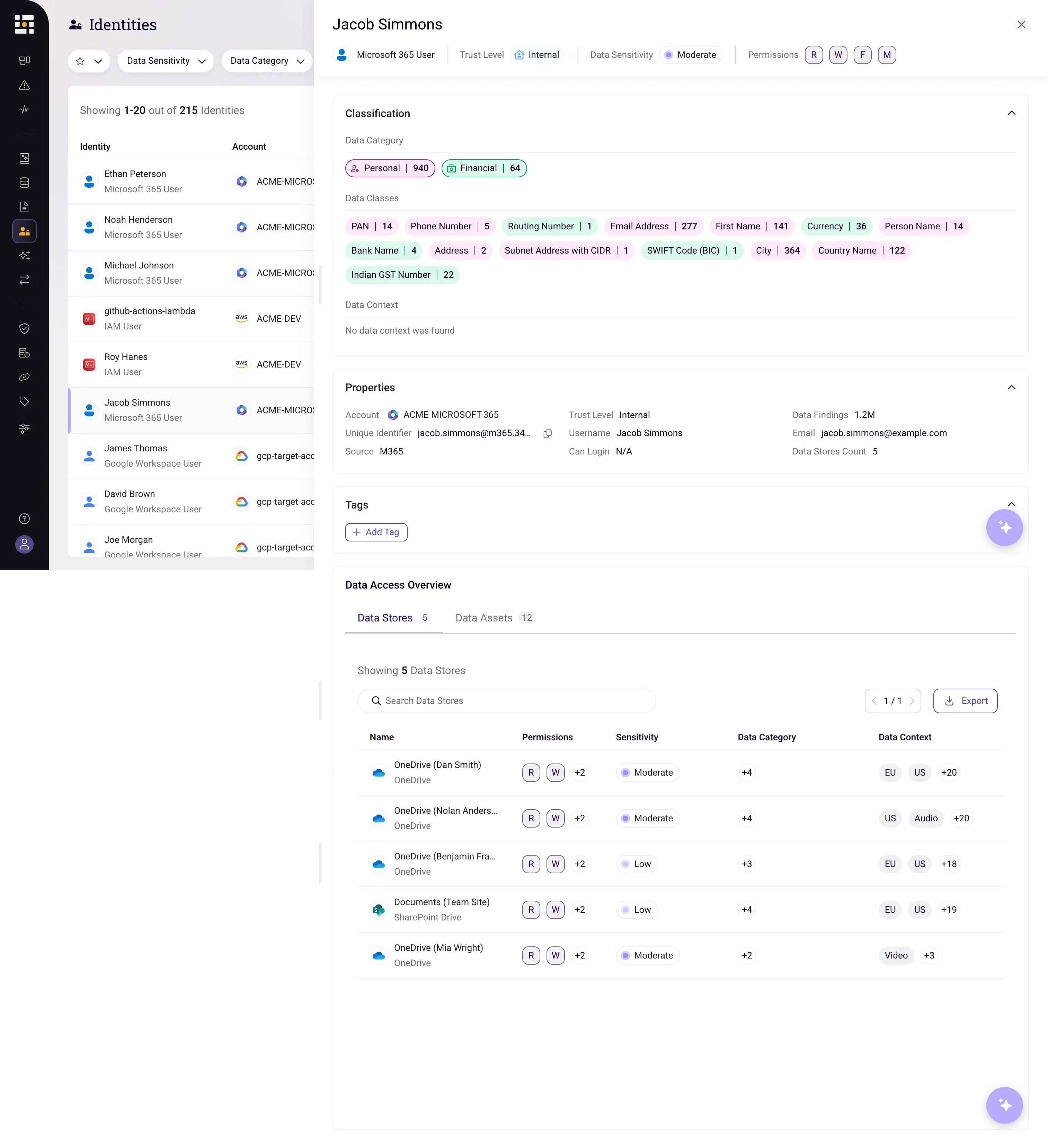
Sentra's DSPM solution leverages advanced AI technologies (like OCR, NER, and embeddings) to automatically discover and classify sensitive data across your entire Microsoft 365 environment. Our intuitive dashboards quickly highlight redundant files, shadow data, and overexposed folders. What's more, we meticulously map access at the identity level, clearly showing which users can access what specific sensitive data – enabling rapid remediation.
For example, in the screenshot below, you'll see a detailed view of an identity (Jacob Simmons) within our system. This includes a concise summary of the sensitive data classes they can access, alongside a complete list of accessible data stores and data assets.
2. Governance: Control AI Output to Prevent Data Leakage
Even after thorough sanitization, some sensitive data must remain accessible within your environment. This is where robust governance comes in, ensuring that Copilot's output never becomes an unintentional vehicle for sensitive data leakage.
Why Output Governance Matters
Without proper controls, Copilot could inadvertently include sensitive details in its generated content or responses. This risk could lead to unauthorized sharing, unchecked sensitive data sprawl, or severe regulatory breaches. The recent EchoLeak vulnerability, for instance, starkly demonstrated how attackers might exploit AI-generated outputs to silently leak critical information.
Leveraging DLP and Sensitivity Labels
Microsoft 365’s Purview Information Protection and DLP policies are powerful tools that allow organizations to control what Copilot can output. Properly labeled sensitive data, such as documents marked “Confidential – Financial,” prompt Copilot to restrict content output, providing users only with references or links rather than sensitive details.
Sentra’s Governance Capabilities
Sentra automatically classifies your data and intelligently applies MPIP sensitivity labels, directly powering Copilot’s critical DLP policies. Our platform integrates seamlessly with Microsoft Purview, ensuring sensitive files are accurately labeled based on flexible, custom business logic. This guarantees that Copilot's outputs remain fully compliant with your active DLP policies.
Below is an example of Sentra’s MPIP label automation in action, showing how we place sensitivity labels on data assets that contain Facebook profile URLs and credit card numbers belonging to EU citizens, which were modified in the past year:
Additionally, our continuous monitoring and real-time alerts empower organizations to immediately address policy violations – for instance, sensitive data with missing or incorrect MPIP labels – helping you maintain audit readiness and seamless compliance alignment.
.webp)
A Data-Centric Security Approach to AI Adoption
By strategically combining robust sanitization and strong governance, you ensure your regulated data remains secure while enabling safe and compliant Copilot adoption across your organization. This approach aligns directly with the core principles outlined by NIST and the EU AI Act, effectively translating high-level compliance guidance into actionable, practical controls.
At Sentra, our mission is clear: to empower secure AI innovation through comprehensive data visibility and truly automated compliance. Our cutting-edge solutions provide the transparency and granular control you need to confidently embrace Copilot’s powerful capabilities, all without risking costly compliance violations.
Next Steps
Adopting Microsoft 365 Copilot securely doesn’t have to be complicated. By leveraging Sentra’s comprehensive DSPM solutions, your organization can create a secure environment where Copilot can safely enhance productivity without ever exposing your regulated data.
Ready to take control? Contact a Sentra expert today to learn more about seamlessly securing your sensitive data and confidently deploying Microsoft 365 Copilot.
<blogcta-big>










.webp)
