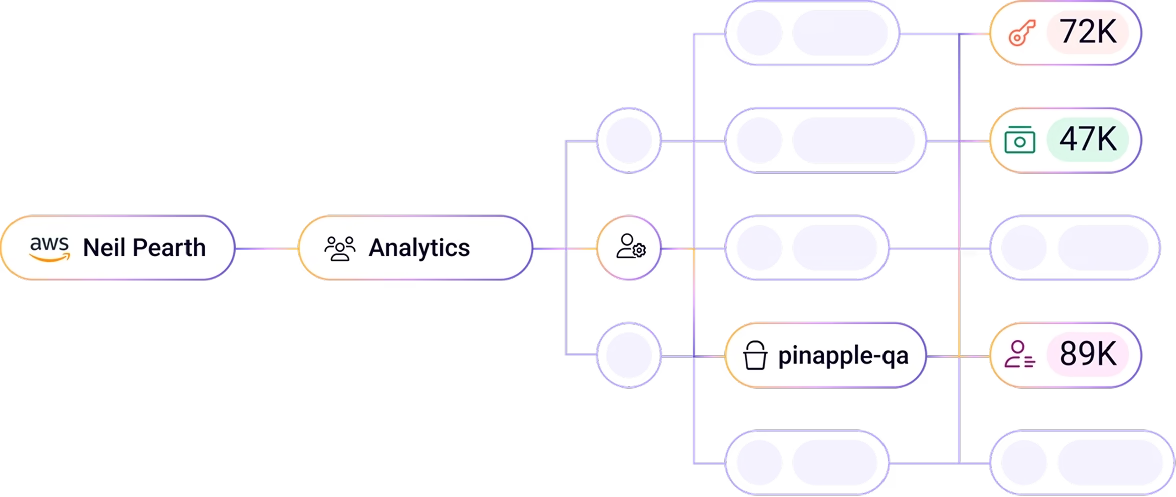
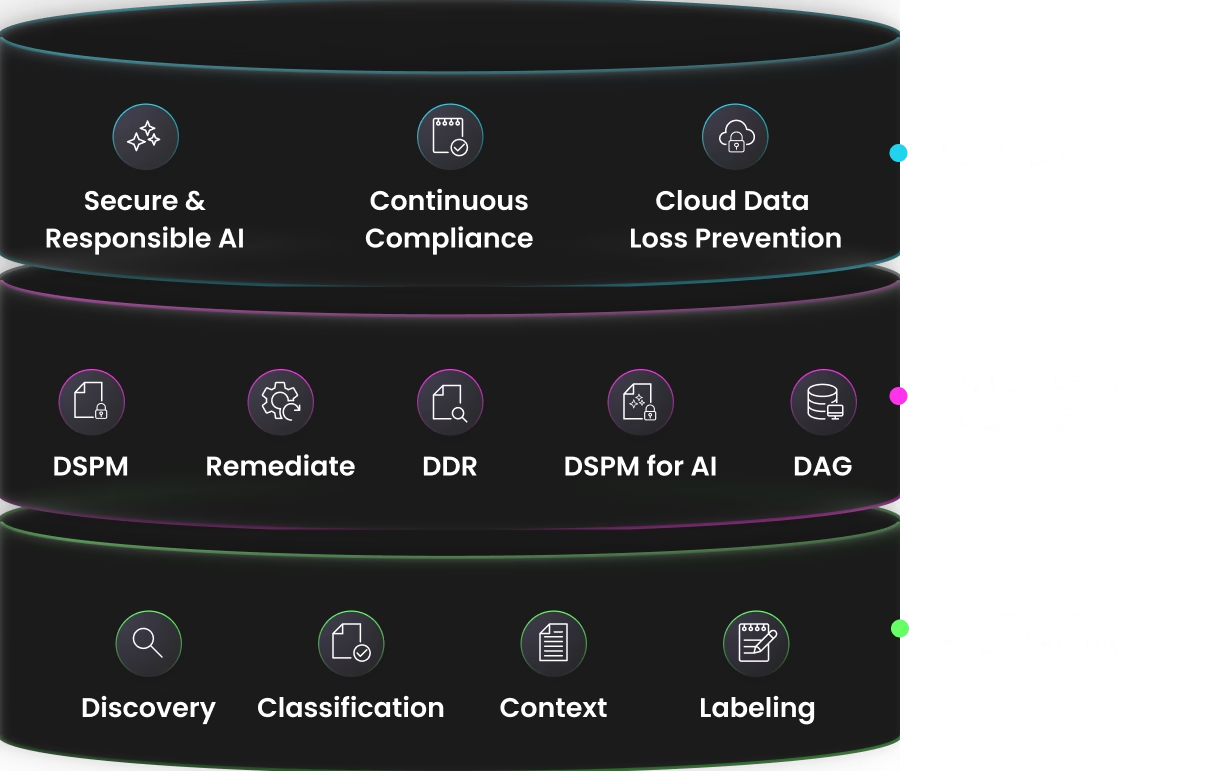
Activate controls via integrations with IAM and DLP systems (revoke access, de-identify data, etc.)

Manage access issues such as excessive permissions, unauthorized access, support least privilege access control

Flag high-risk identities and proactively prevent access control risks