CVE-2025-53770: A Wake-Up Call for Every SharePoint Customer
A vulnerability like this doesn’t just compromise infrastructure, it compromises trust. When attackers gain unauthenticated access to SharePoint, they’re not just landing on a server. They’re landing on contracts, financials, customer records, and source code - the very data that defines your business.
The latest zero-day targeting Microsoft SharePoint is a prime example. It’s not only critical in severity - it’s being actively exploited in the wild, giving threat actors a direct path to your most sensitive data.
Here’s what we know so far.
What Happened in the Sharepoint Zero-Day Attack?
On July 20, 2025, CISA confirmed that attackers are actively exploiting CVE-2025-53770, a remote-code-execution (RCE) zero-day that affects on-premises Microsoft SharePoint servers.
The flaw is unauthenticated and rated CVSS 9.8, letting threat actors run arbitrary code and access every file on the server - no credentials required.
Security researchers have tied the exploits to the “ToolShell” attack chain, which steals SharePoint machine keys and forges trusted ViewState payloads, making lateral movement and persistence dangerously easy.
Microsoft has issued temporary guidance (enabling AMSI, deploying Defender AV, or isolating servers) while it rushes a full patch. Meanwhile, CISA has added CVE-2025-53770 to its Known Exploited Vulnerabilities (KEV) catalog and urges immediate mitigations. CISA
Why Exploitation Is Alarmingly Easy
Attackers don’t need stolen credentials, phishing emails, or sophisticated malware. A typical adversary can move from a list of targets to full SharePoint server control in four quick moves:
- Harvest likely targets in bulk
Public scanners like Censys, Shodan, and certificate transparency logs reveal thousands of company domains exposing SharePoint over HTTPS. A few basic queries surface sharepoint. subdomains or endpoints responding with the SharePoint logo or X-SharePointHealthScore header. - Check for a SharePoint host
If a domain like sharepoint.example.com shows the classic SharePoint sign-in page, it’s likely running ASP.NET and listening on TCP 443—indicating a viable target. - Probe the vulnerable endpoint
A simple GET request to /_layouts/15/ToolPane.aspx?DisplayMode=Edit should return HTTP 200 OK (instead of redirecting to login) on unpatched servers. This confirms exposure to the ToolShell exploit chain. - Send one unauthenticated POST
The vulnerability lies in how SharePoint deserializes __VIEWSTATE data. With a single forged POST request, the attacker gains full RCE—no login, no MFA, no further interaction.
That’s it. From scan to shell can take under five minutes, which is why CISA urged admins to disconnect public-facing servers until patched.
Why Data Security Leaders Should Care
SharePoint is where contracts, customer records, and board decks live. An RCE on the platform is a direct path to your crown jewel data:
- Unbounded blast radius: Compromised machine keys let attackers impersonate any user and exfiltrate sensitive files at scale.
- Shadow exposure: Even if you patch tomorrow, every document the attacker touched today is already outside your control.
- Compliance risk: GDPR, HIPAA, SOX, and new AI-safety rules all require provable evidence of what data was accessed and when.
While vulnerability scanners stop at “patch fast,” data security teams need more visibility into what was exposed, how sensitive it was, and how to contain the fallout. That’s exactly what Sentra’s Data Security Posture Management (DSPM) platform delivers.
How Sentra DSPM Neutralizes the Impact of CVE-2025-53770
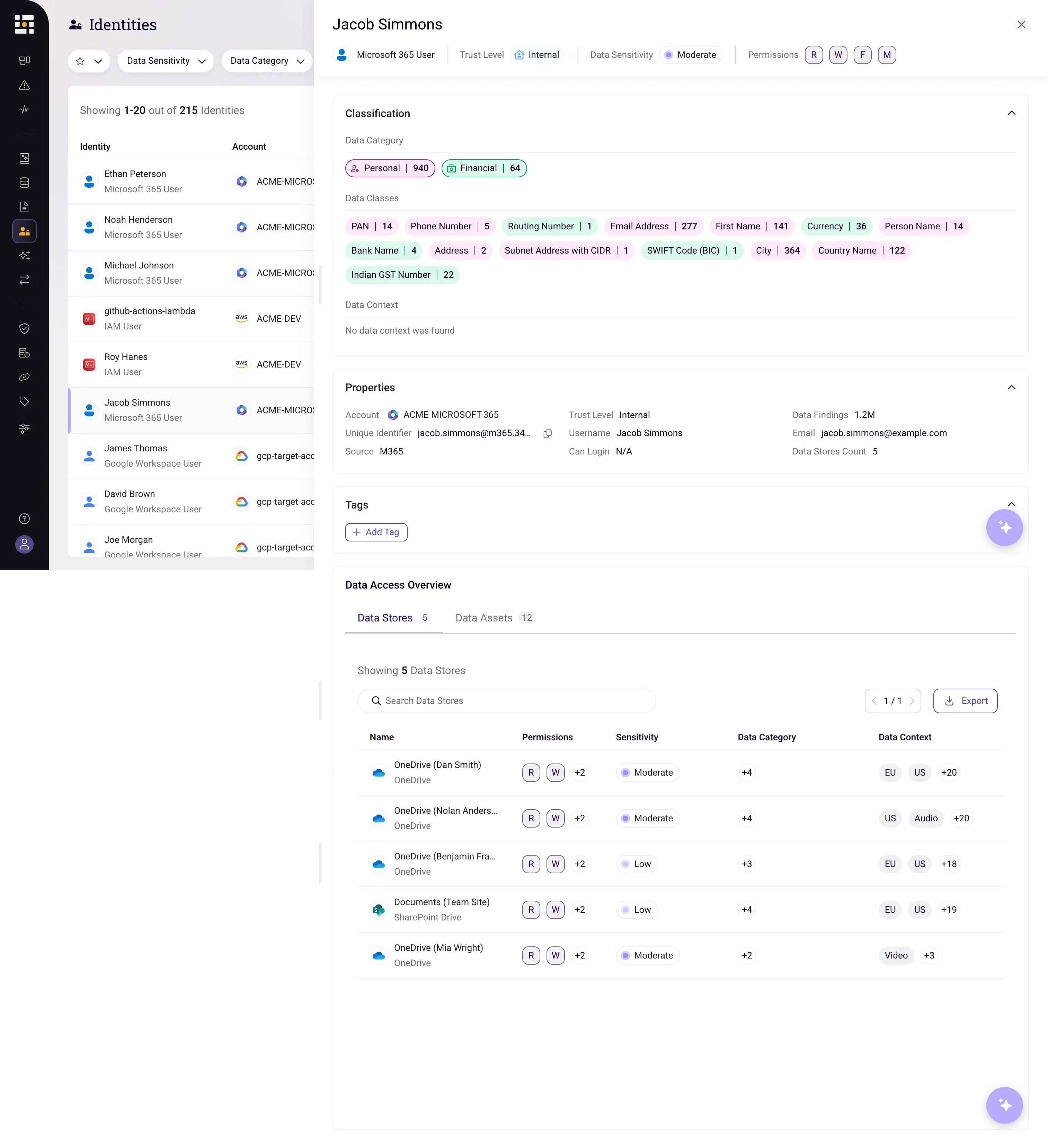
- Continuous data discovery & classification: Sentra’s agentless scanner pinpoints every sensitive file - PII, PHI, intellectual-property, even AI model weights - across on-prem SharePoint, SharePoint Online, Teams, and OneDrive. No blind spots.
- Posture-driven risk mapping: Sentra pinpoints sensitive data sitting on exploitable servers, open to the public, or granted excessive permissions, then automatically routes actionable alerts into your security team’s existing workflow platform.
- Real-time threat detection: Sentra’s Data Detection and Response (DDR) instantly flags unusual access patterns to sensitive data, enabling your team to intervene before risk turns into breach.
- Blast-radius analysis: Sentra shows which regulated data could have been accessed during the exploit window - crucial for incident response and breach notifications.
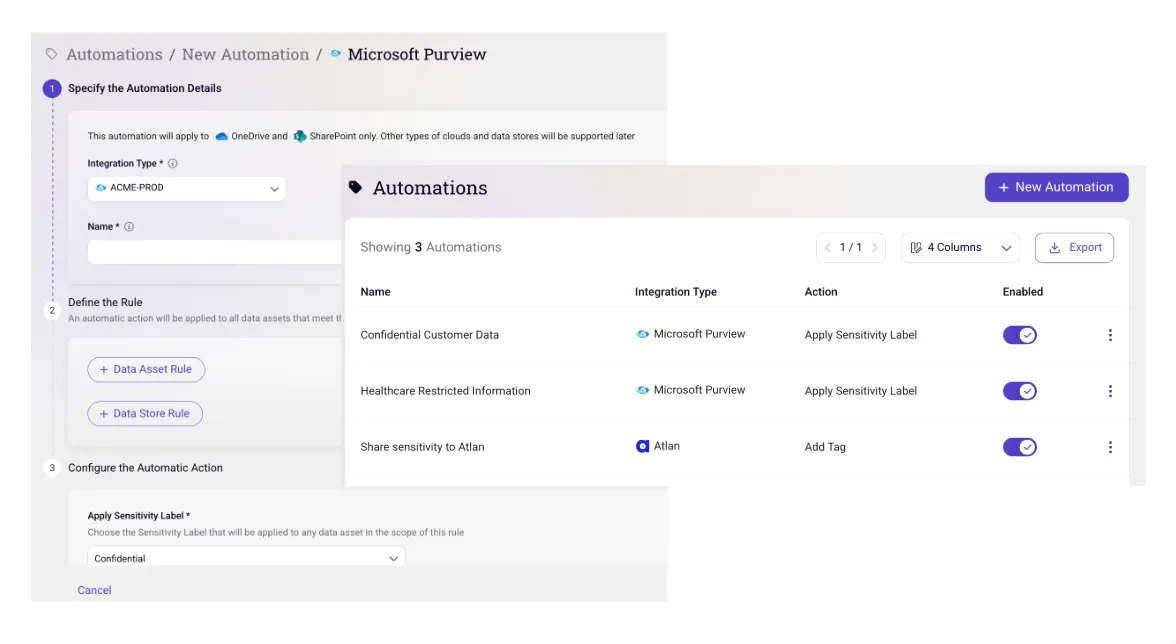
- Automated workflows: Sentra integrates with Defender, Microsoft Purview, Splunk, CrowdStrike, and all leading SOARs to quarantine docs, rotate machine keys, or trigger legal hold—no manual steps required.
- Attacker-resilience scoring: Executive dashboards translate SharePoint misconfigurations into dollar-value risk reduction and compliance posture—perfect for board updates after high-profile CVEs.
What This Means for Your Security Team
CVE-2025-53770 won’t be the last time attackers weaponize a collaboration platform you rely on every day. With Sentra DSPM, you know exactly where your sensitive data is, how exposed it is, and how to shrink that exposure continuously.
With Sentra DSPM, you gain more than visibility. You get the ability to map your most sensitive data, detect threats in real time, and respond with confidence - all while proving compliance and minimizing business impact.
It’s not just about patching faster. It’s about defending what matters most: your data.
Get our checklist on how Sentra DSPM helps neutralize SharePoint zero-day risks and protects your most critical data before the next exploit hits.
<blogcta-big>









.webp)

.webp)
.webp)
