Nikki Ralston
Nikki Ralston is Senior Product Marketing Manager at Sentra, with over 20 years of experience bringing cybersecurity innovations to global markets. She works at the intersection of product, sales, and markets translating complex technical solutions into clear value. Nikki is passionate about connecting technology with users to solve hard problems.
Name's Data Security Posts


DSPM Dirty Little Secrets: What Vendors Don’t Want You to Test
DSPM Dirty Little Secrets: What Vendors Don’t Want You to Test
Discover What DSPM Vendors Try to Hide
Your goal in running a data security/DSPM POV is to evaluate all important performance and cost parameters so you can make the best decision and avoid unpleasant surprises. Vendors, on the other hand, are looking for a ‘quick win’ and will often suggest shortcuts like using a limited test data set and copying your data to their environment.
On the surface this might sound like a reasonable approach, but if you don’t test real data types and volumes in your own environment, the POV process may hide costly failures or compliance violations that will quickly become apparent in production. A recent evaluation of Sentra versus another top emerging DSPM exposed how the other solution’s performance dropped and costs skyrocketed when deployed at petabyte scale. Worse, the emerging DSPM removed data from the customer environment - a clear controls violation.
If you want to run a successful POV and avoid DSPM buyers' remorse you need to look out for these "dirty little secrets".
Dirty Little Secret #1:
‘Start small’ can mean ‘fails at scale’
The biggest 'dirty secret' is that scalability limits are hidden behind the 'start small' suggestion. Many DSPM platforms cannot scale to modern petabyte-sized data environments. Vendors try to conceal this architectural weakness by encouraging small, tightly scoped POVs that never stress the system and create false confidence. Upon broad deployment, this weakness is quickly exposed as scans slow and refresh cycles stretch, forcing teams to drastically reduce scope or frequency. This failure is fundamentally architectural, lacking parallel orchestration and elastic execution, proving that the 'start small' advice was a deliberate tactic to avoid exposing the platform’s inevitable bottleneck.In a recent POV, Sentra successfully scanned 10x more data in approximately the same time than the alternative:
Dirty Little Secret #2:
High cloud cost breaks continuous security
Another reason some vendors try to limit the scale of POVs is to hide the real cloud cost of running them in production. They often use brute-force scanning that reads excessive data, consumes massive compute resources, and is architecturally inefficient. This is easy to mask during short, limited POVs, but quickly drives up cloud bills in production. The resulting cost pressure forces organizations to reduce scan frequency and scope, quietly shifting the platform from continuous security control to periodic inventory. Ultimately, tools that cannot scale scanners efficiently on-demand or scan infrequently trade essential security for cost, proving they are only affordable when they are not fully utilized. In a recent POV run on 100 petabytes of data, Sentra proved to be 10x more operationally cost effective to run:
Dirty Little Secret #3:
‘Good enough’ accuracy degrades security
Accuracy is fundamental to Data Security Posture Management (DSPM) and should not be compromised. While a few points difference may not seem like a deal breaker, every percentage point of classification accuracy can dramatically affect all downstream security controls. Costs increase as manual intervention is required to address FPs. When organizations automate controls based on these inaccuracies, the DSPM platform becomes a source of risk. Confidence is lost. The secret is kept safe because the POV never validates the platform's accuracy against known sensitive data.
In a recent POV Sentra was able to prove less than one percent rate of false positives and false negatives:
DSPM POV Red Flags
- Copy data to the vendor environment for a “quick win”
- Limit features or capabilities to simplify testing
- Artificially reduce the size of scanned data
- Restrict integrations to avoid “complications”
- Limit or avoid API usage
These shortcuts don’t make a POV easier - they make it misleading.
Four DSPM POV Requirements That Expose the Truth
If you want a DSPM POV that reflects production reality, insist on these requirements:
1. Scalability
Run discovery and classification on at least 1 petabyte of real data, including unstructured object storage. Completion time must be measured in hours or days - not weeks.
2. Cost Efficiency
Operate scans continuously at scale and measure actual cloud resource consumption. If cost forces reduced frequency or scope, the model is unsustainable.
3. Accuracy
Validate results against known sensitive data. Measure false positives and false negatives explicitly. Accuracy must be quantified and repeatable.
4. Unstructured Data Depth
Test long-form, heterogeneous, real-world unstructured data including audio, video, etc. Classification must demonstrate contextual understanding, not just keyword matches.
A DSPM solution that only performs well in a limited POV will lead to painful, costly buyer’s regret. Once in production, the failures in scalability, cost efficiency, accuracy, and unstructured data depth quickly become apparent.
Getting ready to run a DSPM POV? Schedule a demo.
<blogcta-big>


How to Choose a Data Access Governance Tool
How to Choose a Data Access Governance Tool
Introduction: Why Data Access Governance Is Harder Than It Should Be
Data access governance should be simple: know where your sensitive data lives, understand who has access to it, and reduce risk without breaking business workflows. In practice, it’s rarely that straightforward. Modern organizations operate across cloud data stores, SaaS applications, AI pipelines, and hybrid environments. Data moves constantly, permissions accumulate over time, and visibility quickly degrades. Many teams turn to data access governance tools expecting clarity, only to find legacy platforms that are difficult to deploy, noisy, or poorly suited for dynamic, fast-proliferating cloud environments.
A modern data access governance tool should provide continuous visibility into who and what can access sensitive data across cloud and SaaS environments, and help teams reduce overexposure safely and incrementally.
What Organizations Actually Need from Data Access Governance
Before evaluating vendors, it’s important to align on outcomes, just not features. Most teams are trying to solve the same core problems:
- Unified visibility across cloud data stores, SaaS platforms, and hybrid environments
- Clear answers to “which identities have access to what, and why?”
- Risk-based prioritization instead of long, unmanageable lists of permissions
- Safe remediation that tightens access without disrupting workflows
Tools that focus only on periodic access reviews or static policies often fall short in dynamic environments where data and permissions change constantly.
Why Legacy and Over-Engineered Tools Fall Short
Many traditional data governance and IGA tools were designed for on-prem environments and slower change cycles. In cloud and SaaS environments, these tools often struggle with:
- Long deployment timelines and heavy professional services requirements
- Excessive alert noise without clear guidance on what to fix first
- Manual access certifications that don’t scale
- Limited visibility into modern SaaS and cloud-native data stores
Overly complex platforms can leave teams spending more time managing the tool than reducing actual data risk.
Key Capabilities to Look for in a Modern Data Access Governance Tool
1. Continuous Data Discovery and Classification
A strong foundation starts with knowing where sensitive data lives. Modern tools should continuously discover and classify data across cloud, SaaS, and hybrid environments using automated techniques, not one-time scans.
2. Access Mapping and Exposure Analysis
Understanding data sensitivity alone isn’t enough. Tools should map access across users, roles, applications, and service accounts to show how sensitive data is actually exposed.
3. Risk-Based Prioritization
Not all exposure is equal. Effective platforms correlate data sensitivity with access scope and usage patterns to surface the highest-risk scenarios first, helping teams focus remediation where it matters most.
4. Low-Friction Deployment
Look for platforms that minimize operational overhead:
- Agentless or lightweight deployment models
- Fast time-to-value
- Minimal disruption to existing workflows
5. Actionable Remediation Workflows
Visibility without action creates frustration. The right tool should support guided remediation, tightening access incrementally and safely rather than enforcing broad, disruptive changes.
How Teams Are Solving This Today
Security teams that succeed tend to adopt platforms that combine data discovery, access analysis, and real-time risk detection in a single workflow rather than stitching together multiple legacy tools. For example, platforms like Sentra focus on correlating data sensitivity with who or what can actually access it, making it easier to identify over-permissioned data, toxic access combinations, and risky data flows, without breaking existing workflows or requiring intrusive agents.
The common thread isn’t the tool itself, but the ability to answer one question continuously:
“Who can access our most sensitive data right now, and should they?”
Teams using these approaches often see faster time-to-value and more actionable insights compared to legacy systems.
Common Gotchas to Watch Out For
When evaluating tools, buyers often overlook a few critical issues:
- Hidden costs for deployment, tuning, or ongoing services
- Tools that surface risk but don’t help remediate it
- Point-in-time scans that miss rapidly changing environments
- Weak integration with identity systems, cloud platforms, and SaaS apps
Asking vendors how they handle these scenarios during a pilot can prevent surprises later.
Download The Dirt on DSPM POVs: What Vendors Don’t Want You to Know
How to Run a Successful Pilot
A focused pilot is the best way to evaluate real-world effectiveness:
- Start with one or two high-risk data stores
- Measure signal-to-noise, not alert volume
- Validate that remediation steps work with real teams and workflows
- Assess how quickly the tool delivers actionable insights
The goal is to prove reduced risk, not just improved reporting.
Final Takeaway: Visibility First, Enforcement Second
Effective data access governance starts with visibility. Organizations that succeed focus first on understanding where sensitive data lives and how it’s exposed, then apply controls gradually and intelligently. Combining DAG with DSPM is an effective way to achieve this.
In 2026, the most effective data access governance tools are continuous, risk-driven, and cloud-native, helping security teams reduce exposure without slowing the business down.
Frequently Asked Questions (FAQs)
What is data access governance?
Data access governance is the practice of managing and monitoring who can access sensitive data, ensuring access aligns with business needs and security requirements.
How is data access governance different from IAM?
IAM focuses on identities and permissions. Data access governance connects those permissions to actual data sensitivity and exposure, and alerts when violations occur.
How do organizations reduce over-permissioned access safely?
By using risk-based prioritization and incremental remediation instead of broad access revocations.
What should teams look for in a modern data access governance tool?
This question comes up frequently in real-world evaluations, including Reddit discussions where teams share what’s worked and what hasn’t. Teams should prioritize tools that give fast visibility into who can access sensitive data, provide context-aware insights, and allow incremental, safe remediation - all without breaking workflows or adding heavy operational overhead. Cloud- and SaaS-aware platforms tend to outperform legacy or overly complex solutions.
<blogcta-big>


One Platform to Secure All Data: Moving from Data Discovery to Full Data Access Governance
One Platform to Secure All Data: Moving from Data Discovery to Full Data Access Governance
The cloud has changed how organizations approach data security and compliance. Security leaders have mostly figured out where their sensitive data is, thanks to data security posture management (DSPM) tools. But that's just the beginning. Who can access your data? What are they doing with it?
Workloads and sensitive assets now move across multi-cloud, hybrid, and SaaS environments, increasing the need for control over access and use. Regulators, boards, and customers expect more than just awareness. They want real proof that you are governing access, lowering risk, and keeping cloud data secure. The next priority is here: shifting from just knowing what data you have to actually governing access to it. Sentra provides a unified platform designed for this shift.
Why Discovery Alone Falls Short in the Cloud Era
DSPM solutions make it possible to locate, classify, and monitor sensitive data almost anywhere, from databases to SaaS apps. This visibility is valuable, particularly as organizations manage more data than ever. Over half of enterprises have trouble mapping their full data environment, and 85% experienced a data loss event in the past year.
But simply seeing your data won’t do the job. DSPM can point out risks, like unencrypted data or exposed repositories, but it usually can’t control access or enforce policies in real time. Cloud environments change too quickly for static snapshots and scheduled reviews. Effective security means not only seeing your data but actively controlling who can reach it and what they can do.
Data Access Governance: The New Frontier for Cloud Data Security
Data Access Governance (DAG) covers processes and tools that constantly monitor, control, and audit who can access your data, how, and when, wherever it lives in the cloud.
Why does DAG matter so much now? Consider some urgent needs:
- Compliance and Auditability: 82% of organizations rank compliance as their top cloud concern. Data access controls and real-time audit logs make it possible to demonstrate compliance with GDPR, HIPAA, and other data laws.
- Risk Reduction: Cloud environments change constantly, so outdated access policies quickly become a problem. DAG enforces least-privilege access, supports just-in-time permissions, and lets teams quickly respond to risky activity.
- AI and New Threats: As generative AI becomes more common, concerns about misuse and unsupervised data access are growing. Forty percent of organizations now see AI as a data leak risk.
DAG gives organizations a current view of “who has access to my data right now?” for both employees and AI agents, and allows immediate changes if permissions or risks shift.
The Power of a Unified, Agentless Platform for DSPM and DAG
Why should security teams look for a unified platform instead of another narrow tool? Most large companies use several clouds, with 83% managing more than one, but only 34% have unified compliance. Legacy tools focused on discovery or single clouds aren’t enough.
Sentra’s agentless, multi-cloud solution meets these needs directly. With nothing extra to install or maintain, Sentra provides:
- Automated discovery and classification of data in AWS, Azure, GCP, and SaaS
- Real-time mapping and management of every access, from users to services and APIs
- Policy-as-code for dynamic enforcement of least-privilege access
- Built-in detection and response that moves beyond basic rules
This approach combines data discovery with ongoing access management, helping organizations save time and money. It bridges the gaps between security, compliance, and DevOps teams. GlobalNewswire projects the global market for unified data governance will exceed $15B by 2032. Companies are looking for platforms that can keep things simple and scale with growth.
Strategic Benefits: From Reduced Risk to Business Enablement
What do organizations actually achieve with cloud-native, end-to-end data access governance?
- Operational Efficiency: Replace slow, manual reviews and separate tools. Automate access reviews, policy enforcement, and compliance, all in one platform.
- Faster Remediation and Lower TCO: Real-time alerts pinpoint threats faster, and automation speeds up response and reduces resource needs.
- Future-Proof Security: Designed to handle multi-cloud and AI demands, with just-in-time access, zero standing privilege, and fast threat response.
- Business Enablement and Audit Readiness: Central visibility and governance help teams prepare for audits faster, gain customer trust, and safely launch digital products.
In short, a unified platform for DSPM and DAG is more than a tech upgrade, it gives security teams the ability to directly support business growth and agility.
Why Sentra: The Converged Platform for Modern Data Security
Sentra covers every angle: agentless discovery, continuous access control, ongoing threat detection, and compliance, all within one platform. Sentra unites DSPM, DAG, and Data Detection & Response (DDR) in a single solution.
With Sentra, you can:
- Stop relying on periodic reviews and move to real-time governance
- See and manage data across all cloud and SaaS services
- Make compliance easier while improving security and saving money
Conclusion
Data discovery is just the first step to securing cloud data. For compliance, resilience, and agility, organizations need to go beyond simply finding data and actually managing who can use it. DSPM isn’t enough anymore, full Data Access Governance is now a must.
Sentra’s agentless platform gives security and compliance teams a way to find, control, and protect sensitive cloud data, with full oversight along the way. Make the switch now and turn cloud data security into an asset for your business.
Looking to bring all your cloud data security and access control together? Request a Sentra demo to see how it works, or watch a 5-minute product demo for more on how Sentra helps organizations move from discovery to full data governance.
<blogcta-big>


Sentra Is One of the Hottest Cybersecurity Startups
Sentra Is One of the Hottest Cybersecurity Startups
We knew we were on a hot streak, and now it’s official.
Sentra has been named one of CRN’s 10 Hottest Cybersecurity Startups of 2025. This recognition is a direct reflection of our commitment to redefining data security for the cloud and AI era, and of the growing trust forward-thinking enterprises are placing in our unique approach.
This milestone is more than just an award. It shows our relentless drive to protect modern data systems and gives us a chance to thank our customers, partners, and the Sentra team whose creativity and determination keep pushing us ahead.
The Market Forces Fueling Sentra’s Momentum
Cybersecurity is undergoing major changes. With 94% of organizations worldwide now relying on cloud technologies, the rapid growth of cloud-based data and the rise of AI agents have made security both more urgent and more complicated. These shifts are creating demands for platforms that combine unified data security posture management (DSPM) with fast data detection and response (DDR).
Industry data highlights this trend: over 73% of enterprise security operations centers are now using AI for real-time threat detection, leading to a 41% drop in breach containment time. The global cybersecurity market is growing rapidly, estimated to reach $227.6 billion in 2025, fueled by the need to break down barriers between data discovery, classification, and incident response 2025 cybersecurity market insights. In 2025, organizations will spend about 10% more on cyber defenses, which will only increase the demand for new solutions.
Why Recognition by CRN Matters and What It Means
Landing a place on CRN’s 10 Hottest Cybersecurity Startups of 2025 is more than publicity for Sentra. It signals we truly meet the moment. Our rise isn’t just about new features; it’s about helping security teams tackle the growing risks posed by AI and cloud data head-on. This recognition follows our mention as a CRN 2024 Stellar Startup, a sign of steady innovation and mounting interest from analysts and enterprises alike.
Being on CRN’s list means customers, partners, and investors value Sentra’s straightforward, agentless data protection that helps organizations work faster and with more certainty.
Innovation Where It Matters: Sentra’s Edge in Data and AI Security
Sentra stands out for its practical approach to solving urgent security problems, including:
- Agentless, multi-cloud coverage: Sentra identifies and classifies sensitive data and AI agents across cloud, SaaS, and on-premises environments without any agents or hidden gaps.
- Integrated DSPM + DDR: We go further than monitoring posture by automatically investigating incidents and responding, so security teams can act quickly on why DSPM+DDR matters.
- AI-driven advancements: Features like domain-specific AI Classifiers for Unstructure advanced AI classification leveraging SLMs, Data Security for AI Agents and Microsoft M365 Copilot help customers stay in control as they adopt new technologies Sentra’s AI-powered innovation.
With new attack surfaces popping up all the time, from prompt injection to autonomous agent drift, Sentra’s architecture is built to handle the world of AI.
A Platform Approach That Outpaces the Competition
There are plenty of startups aiming to tackle AI, cloud, and data security challenges. Companies like 7AI, Reco, Exaforce, and Noma Security have been in the news for their funding rounds and targeted solutions. Still, very few offer the kind of unified coverage that sets Sentra apart.
Most competitors stick to either monitoring SaaS agents or reducing SOC alerts. Sentra does more by providing both agentless multi-cloud DSPM and built-in DDR. This gives organizations visibility, context, and the power to act in one platform. With features like Data Security for AI Agents, Sentra helps enterprises go beyond managing alerts by automating meaningful steps to defend sensitive data everywhere.
Thanks to Our Community and What’s Next
This honor belongs first and foremost to our community: customers breaking new ground in data security, partners building solutions alongside us, and a team with a clear goal to lead the industry.
If you haven’t tried Sentra yet, now’s a great time to see what we can do for your cloud and AI data security program. Find out why we’re at the forefront: schedule a personalized demo or read CRN’s full 2025 list for more insight.
Conclusion
Being named one of CRN’s hottest cybersecurity startups isn’t just a milestone. It pushes us forward toward our vision - data security that truly enables innovation. The market is changing fast, but Sentra’s focus on meaningful security results hasn't wavered.
Thank you to our customers, partners, investors, and team for your ongoing trust and teamwork. As AI and cloud technology shape the future, Sentra is ready to help organizations move confidently, securely, and quickly.
<blogcta-big>


Third-Party OAuth Apps Are the New Shadow Data Risk: Lessons from the Gainsight/Salesforce Incident
Third-Party OAuth Apps Are the New Shadow Data Risk: Lessons from the Gainsight/Salesforce Incident
The recent exposure of customer data through a compromised Gainsight integration within Salesforce environments is more than an isolated event - it’s a sign of a rapidly evolving class of SaaS supply-chain threats. Even trusted AppExchange partners can inadvertently create access pathways that attackers exploit, especially when OAuth tokens and machine-to-machine connections are involved. This post explores what happened, why today’s security tooling cannot fully address this scenario, and how data-centric visibility and identity governance can meaningfully reduce the blast radius of similar breaches.
A Recap of the Incident
In this case, attackers obtained sensitive credentials tied to a Gainsight integration used by multiple enterprises. Those credentials allowed adversaries to generate valid OAuth tokens and access customer Salesforce orgs, in some cases with extensive read capabilities. Neither Salesforce nor Gainsight intentionally misconfigured their systems. This was not a product flaw in either platform. Instead, the incident illustrates how deeply interconnected SaaS environments have become and how the security of one integration can impact many downstream customers.
Understanding the Kill Chain: From Stolen Secrets to Salesforce Lateral Movement
The attackers’ pathway followed a pattern increasingly common in SaaS-based attacks. It began with the theft of secrets; likely API keys, OAuth client secrets, or other credentials that often end up buried in repositories, CI/CD logs, or overlooked storage locations. Once in hand, these secrets enabled the attackers to generate long-lived OAuth tokens, which are designed for application-level access and operate outside MFA or user-based access controls.
What makes OAuth tokens particularly powerful is that they inherit whatever permissions the connected app holds. If an integration has broad read access, which many do for convenience or legacy reasons, an attacker who compromises its token suddenly gains the same level of visibility. Inside Salesforce, this enabled lateral movement across objects, records, and reporting surfaces far beyond the intended scope of the original integration. The entire kill chain was essentially a progression from a single weakly-protected secret to high-value data access across multiple Salesforce tenants.
Why Traditional SaaS Security Tools Missed This
Incident response teams quickly learned what many organizations are now realizing: traditional CASBs and CSPMs don’t provide the level of identity-to-data context necessary to detect or prevent OAuth-driven supply-chain attacks.
CASBs primarily analyze user behavior and endpoint connections, but OAuth apps are “non-human identities” - they don’t log in through browsers or trigger interactive events. CSPMs, in contrast, focus on cloud misconfigurations and posture, but they don’t understand the fine-grained data models of SaaS platforms like Salesforce. What was missing in this incident was visibility into how much sensitive data the Gainsight connector could access and whether the privileges it held were appropriate or excessive. Without that context, organizations had no meaningful way to spot the risk until the compromise became public.
Sentra Helps Prevent and Contain This Attack Pattern
Sentra’s approach is fundamentally different because it starts with data: what exists, where it resides, who or what can access it, and whether that access is appropriate. Rather than treating Salesforce or other SaaS platforms as black boxes, Sentra maps the data structures inside them, identifies sensitive records, and correlates that information with identity permissions including third-party apps, machine identities, and OAuth sessions.
One key pillar of Sentra’s value lies in its DSPM capabilities. The platform identifies sensitive data across all repositories, including cloud storage, SaaS environments, data warehouses, code repositories, collaboration platforms, and even on-prem file systems. Because Sentra also detects secrets such as API keys, OAuth credentials, private keys, and authentication tokens across these environments, it becomes possible to catch compromised or improperly stored secrets before an attacker ever uses them to access a SaaS platform.
Another area where this becomes critical is the detection of over-privileged connected apps. Sentra continuously evaluates the scopes and permissions granted to integrations like Gainsight, identifying when either an app or an identity holds more access than its business purpose requires. This type of analysis would have revealed that a compromised integrated app could see far more data than necessary, providing early signals of elevated risk long before an attacker exploited it.
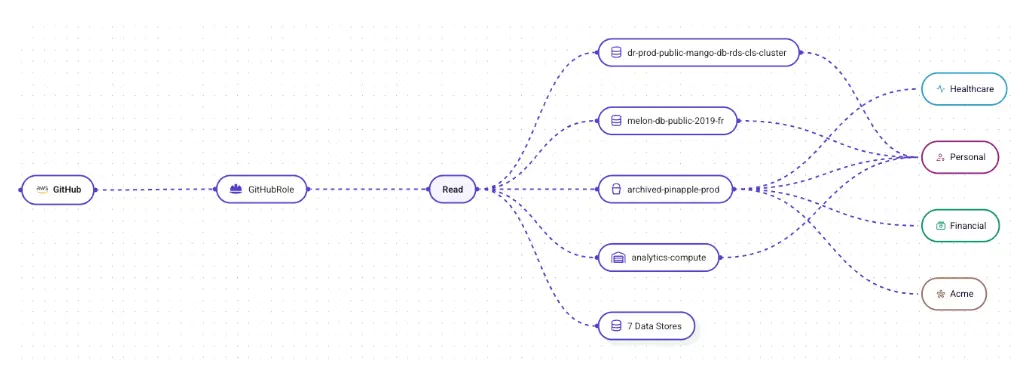
Sentra further tracks the health and behavior of non-human identities. Service accounts and connectors often rely on long-lived credentials that are rarely rotated and may remain active long after the responsible team has changed. Sentra identifies these stale or overly permissive identities and highlights when their behavior deviates from historical norms. In the context of this incident type, that means detecting when a connector suddenly begins accessing objects it never touched before or when large volumes of data begin flowing to unexpected locations or IP ranges.
Finally, Sentra’s behavior analytics (part of DDR) help surface early signs of misuse. Even if an attacker obtains valid OAuth tokens, their data access patterns, query behavior, or geography often diverge from the legitimate integration. By correlating anomalous activity with the sensitivity of the data being accessed, Sentra can detect exfiltration patterns in real time—something traditional tools simply aren’t designed to do.
The 2026 Outlook: More Incidents Are Coming
The Gainsight/Salesforce incident is unlikely to be the last of its kind. The speed at which enterprises adopt SaaS integrations far exceeds the rate at which they assess the data exposure those integrations create. OAuth-based supply-chain attacks are growing quickly because they allow adversaries to compromise one provider and gain access to dozens or hundreds of downstream environments. Given the proliferation of partner ecosystems, machine identities, and unmonitored secrets, this attack vector will continue to scale.
Prediction:
Unless enterprises add data-centric SaaS visibility and identity-aware DSPM, we should expect three to five more incidents of similar magnitude before summer 2026.
Conclusion
The real lesson from the Gainsight/Salesforce breach is not to reduce reliance on third-party SaaS providers as modern business would grind to a halt without them. The lesson is that enterprises must know where their sensitive data lives, understand exactly which identities and integrations can access it, and ensure those privileges are continuously validated. Sentra provides that visibility and contextual intelligence, making it possible to identify the risks that made this breach possible and help to prevent the next one.
<blogcta-big>


Securing the Cloud: Advanced Strategies for Continuous Data Monitoring
Securing the Cloud: Advanced Strategies for Continuous Data Monitoring
In today's digital world, data security in the cloud is essential. You rely on popular observability tools to track availability, performance, and usage—tools that keep your systems running smoothly. However, as your data flows continuously between systems and regions, you need a layer of security that delivers granular insights without disrupting performance.
Cloud service platforms provide the agility and efficiency you expect; however, they often lack the ability to monitor real-time data movement, access, and risk across diverse environments.
This blog post explains how cloud data monitoring strategies protect your data while addressing issues like data sprawl, data proliferation, and unstructured data challenges. Along the way, we will share practical information to help you deepen your understanding and strengthen your overall security posture.
Why Real-Time Cloud Monitoring Matters
In the cloud, data does not remain static. It shifts between environments, services, and geographical locations. As you manage these flows, a critical question arises: "Where is my sensitive cloud data stored?"
Knowing the exact location of your data in real-time is crucial for mitigating unauthorized access, preventing compliance issues, and effectively addressing data sprawl and proliferation.
Risk of Data Misplacement: When Data Is Stored Outside Approved Environments
Misplaced data refers to information stored outside its approved environment. This can occur when data is in unauthorized or unverified cloud instances or shadow IT systems. Such misplacement heightens security risks and complicates compliance efforts.
A simple table can clarify the differences in risk levels and possible mitigation strategies for various data storage environments:
| Data Location | Approved Environment | Risk Level | Example Mitigation Strategy |
|---|---|---|---|
| Authorized Cloud | Yes | Low | Regular Audits |
| Shadow IT Systems | No | High | Immediate remediation |
| Unsecured File Shares | No | Medium | Enhanced access controls |
Risk of Insufficient Monitoring: Gaps in Real-Time Visibility of Rapid Data Movements
The high velocity of data flows in vast cloud environments makes tracking data challenging, and traditional monitoring methods may fall short.
The rapid data movement means that data proliferation often outstrips traditional monitoring efforts. Meanwhile, the sheer volume, variety, and velocity of data require risk analysis tools that are built for scale.
Legacy systems typically struggle with these issues, making it difficult for you to maintain up-to-date oversight and achieve a comprehensive security posture. Explore Sentra's blog on data movement risks for additional details.
Limitations of Legacy Data Security Solutions
When evaluating how to manage and monitor cloud data, it’s clear that traditional security tools fall short in today’s complex, cloud-native environments.
Older security solutions (built for the on-prem era!) were designed for static environments, while today's dynamic cloud demands modern, more scalable approaches. Legacy data classification methods, as discussed in this Sentra analysis, also fail to manage unstructured data effectively.
Let’s take a deeper look at their limitations:
- Inadequate data classification: Traditional data classification often relies on manual processes that fail to keep pace with real-time cloud operations. Manual classification is inefficient and prone to error, making it challenging to quickly identify and secure sensitive information.
- Such outdated methods particularly struggle with unstructured data management, leaving gaps in visibility.
- Scalability issues: As your enterprise grows and embraces the cloud, the volume of data you must handle also grows exponentially. When this happens, legacy systems cannot keep up. They lag behind and are slow to respond to potential risks, exposing your company to possible security breaches.
- Modern requirements for cloud data management and monitoring call for solutions that scale with your business.
- High operational costs: Maintaining outdated security tools can be expensive. Legacy systems often incur high operational costs due to manual oversight, taxing cloud compute consumption, and inefficient processes.
- These costs can escalate quickly, especially compared to cloud-native solutions offering automation, efficiency, and streamlined management.
To address these risks, it's essential to have a strategy that shows you how to monitor data as it moves, ensuring that sensitive files never end up in unapproved environments.
Best Practices for Cloud Data Monitoring and Protection
In an era of rapidly evolving cloud environments, implementing a cohesive cloud data monitoring strategy that integrates actionable recommendations is essential. This approach combines automated data discovery, real-time monitoring, robust access governance, and continuous compliance validation to secure sensitive cloud data and address emerging threats effectively.
Automated Data Discovery and Classification
Implementing an agentless, cloud-native solution enables you to continuously discover and classify sensitive data without any performance drawbacks. Automation significantly reduces manual errors and delivers real-time insights for robust and efficient data monitoring.
Benefits include:
- Continuous data discovery and classification
- Fewer manual interventions
- Real-time risk assessment
- Lower operational costs through automation
- Simplified deployment and ongoing maintenance
- Rapid response to emerging risks with minimal disruption
By adopting a cloud-native data security platform, you gain deeper visibility into your sensitive data without adding system overhead.
Real-Time Data Movement Monitoring
To prevent breaches, real-time cloud monitoring is critical. Receiving real-time alerts will empower you to take action quickly and mitigate threats in the event of unauthorized transfers or suspicious activities.
A well-designed monitoring dashboard can visually display data flows, alert statuses, and remediation actions—all of which provide clear, actionable insights. Alerts can also flow directly to remediation platforms such as ITSM or SOAR systems.
In addition to real-time dashboards, implement automated alerting workflows that integrate with your existing incident response tools. This ensures immediate visibility when anomalies occur for a swift and coordinated response. Continuous monitoring highlights any unusual data movement, helping security teams stay ahead of threats in an environment where data volumes and velocities are constantly expanding.
Robust Access Governance
Only authorized parties should be able to access and utilize sensitive data. Maintain strict oversight by enforcing least privilege access and performing regular reviews. This not only safeguards data but also helps you adhere to the compliance requirements of any relevant regulatory standards.
A checklist for robust governance might include:
- Implementation of role-based and attribute-based access control
- Periodic access audits
- Integration with identity management systems
Ensuring Compliance and Data Privacy
Adhering to data privacy regulations that apply to your sector or location is a must. Continuous monitoring and proactive validation will help you identify and address compliance gaps before your organization is hit with a security breach or legal violation. Sentra offers actionable steps related to various regulations to solidify your compliance posture.
Integrating automated compliance checks into your security processes helps you meet regulatory requirements. To learn more about scaling your security infrastructure, refer to Sentra’s guide to achieving exabyte-scale enterprise data security.
Beyond tools and processes, cultivating a security-minded culture is critical. Conduct regular training sessions and simulated breach exercises so that everyone understands how to handle sensitive data responsibly. Encouraging active participation and accountability across the organization solidifies your security posture, bridging the gap between technical controls and human vigilance.
Sentra Addresses Cloud Data Monitoring Challenges
Sentra's platform complements your current observability tools, enhancing them with robust data security capabilities. Let’s explore how Sentra addresses common challenges in cloud data monitoring.
Exabyte-Scale Mastery: Navigating Expansive Data Ecosystems
Sentra’s platform is designed to handle enormous data volumes with ease. Its distributed architecture and elastic scaling provide comprehensive oversight and ensure high performance as data proliferation intensifies. The platform's distributed architecture and elastic scaling capabilities guarantee high performance, regardless of data volume.
Key features:
- Distributed architecture for high-volume data
- Elastic scaling for dynamic cloud environments
- Integration with primary cloud services
Seamless Automation: Transforming Manual Workflows into Continuous Security
By automating data discovery, classification, and monitoring, Sentra eliminates the need for extensive manual intervention. This streamlined approach provides uninterrupted protection and rapid threat response.
Automation is essential for addressing the challenges of data sprawl without compromising system performance.
Deep Insights & Intelligent Validation: Harnessing Context for Proactive Risk Detection
Sentra distinguishes itself by providing deep contextual analysis of your data. Its intelligent validation process efficiently detects anomalies and prioritizes risks, enabling precise and proactive remediation.
This capability directly addresses the primary concern of achieving continuous, real-time monitoring and ensuring precise, efficient data protection.
Unified Security: Integrating with your Existing Systems for Enhanced Protection
One of the most significant advantages of Sentra's platform is its seamless integration with your current SIEM and SOAR tools. This unified approach allows you to maintain excellent observability with your trusted systems while benefiting from enhanced security measures without any operational disruption.
Conclusion
Effective cloud data monitoring is achieved by blending the strengths of your trusted observability tools with advanced security measures. By automating data discovery and classification, establishing real-time monitoring, and enforcing robust access governance, you can safeguard your data against emerging threats.
Elevate your operations with an extra layer of automated, cloud-native security that tackles data sprawl, proliferation, and compliance challenges. After carefully reviewing your current security and identifying any gaps, invest in modern tools that provide visibility, protection, and resilience.
Maintaining cloud security is a continuous task that demands vigilance, innovation, and proactive decision-making. Integrating solutions like Sentra's platform into your security framework will offer robust, scalable protection that evolves with your business needs. The future of your data security is in your hands, so take decisive steps to build a safer, more secure cloud environment.
<blogcta-big>

Enterprise Data Security
Enterprise Data Security
Enterprise Data Security has evolved from a back-office IT concern into a strategic imperative that defines how organizations compete, innovate, and maintain trust in 2026. As businesses accelerate their adoption of cloud infrastructure, artificial intelligence, and distributed work models, the attack surface has expanded exponentially. Modern enterprises face a dual challenge: securing petabytes of data scattered across hybrid environments while enabling rapid access for AI-driven analytics and collaboration tools. This article explores the comprehensive strategies and architectures that define effective Enterprise Data Security today.
What is Enterprise Data Security?
Enterprise Data Security refers to the comprehensive set of policies, technologies, and processes designed to protect an organization's sensitive information from unauthorized access, breaches, and misuse across all environments, whether on-premises, in the cloud, or within SaaS applications. Unlike traditional perimeter-based security, modern enterprise data security operates on a data-centric model that follows information wherever it moves, ensuring protection is embedded at the data layer rather than relying solely on network boundaries.
The scope encompasses several critical components:
- Data discovery and classification that identifies and categorizes sensitive assets
- Access governance that enforces least-privilege principles and monitors who can reach what data
- Encryption and tokenization that protect data at rest and in transit
- Continuous monitoring that detects anomalous behavior and potential threats in real time
Legal compliance is inseparable from this framework. Regulations such as GDPR, HIPAA, CCPA, and the emerging EU AI Act mandate strict controls over personal data, health information, and AI training datasets, making compliance a fundamental architectural requirement rather than a checkbox exercise.
Why Enterprise Data Security Matters
Organizations today face an unprecedented threat landscape where digital communications and cloud adoption have dramatically increased exposure to cyberattacks, insider threats, and accidental data leaks. A single breach can result in millions of dollars in regulatory fines, irreparable damage to brand reputation, and loss of customer trust. These are all consequences that extend far beyond immediate financial impact.
Proactive data security is essential because reactive measures are no longer sufficient. Attackers exploit misconfigurations, over-permissioned access, and shadow data (forgotten or redundant information that accumulates in cloud storage) to gain footholds within enterprise environments. By the time a breach is detected through traditional means, sensitive data may have already been exfiltrated or encrypted for ransom.
Beyond threat mitigation, enterprise data security enables business innovation. Organizations that maintain complete visibility and control over their data can confidently adopt AI technologies, knowing that sensitive information won't inadvertently train public models or leak through AI-generated outputs. Secure data governance also reduces cloud storage costs by identifying and eliminating redundant, obsolete, or trivial (ROT) data; organizations typically achieve storage cost reductions of approximately 20% while simultaneously improving their security posture.
Enterprise Security Architecture
Modern enterprise security architecture is built on multiple layers of defense that work together to protect data throughout its lifecycle. At the foundation lies network security, including next-generation firewalls that inspect traffic at the application layer, intrusion detection and prevention systems, and secure web gateways that filter malicious content. However, as data increasingly resides outside traditional network perimeters, the architecture has shifted toward identity-centric and data-centric models.
Core Architectural Components
- Multi-factor authentication (MFA) requiring users to verify identity through multiple independent credentials before accessing sensitive systems
- Identity and access management (IAM) platforms that enforce role-based access controls and continuously evaluate permissions to prevent privilege creep
- Sandboxing and micro-segmentation that isolate workloads and limit lateral movement within networks
- Encryption technologies that protect data both at rest and in transit
A critical architectural element in 2026 is the in-environment data security platform. Unlike legacy solutions that require data to be copied to vendor-controlled clouds for analysis, modern architectures scan and classify data in place, within the customer's own infrastructure. This approach eliminates the risk of sensitive data leaving organizational control during security assessments and aligns with regulatory requirements for data residency and sovereignty.
Prevent Sensitive Data Exposure
Preventing sensitive data exposure requires a systematic approach that begins with discovery and classification. Organizations must first determine which data is truly sensitive; whether its personally identifiable information (PII), protected health information (PHI), financial records, or intellectual property, and classify it according to regulatory requirements and business risk.
Key Prevention Strategies
- Data minimization: Only retain information strictly necessary for business operations
- Tokenization and truncation: Replace sensitive data with non-sensitive substitutes or remove unnecessary portions
- Consistent encryption: Apply strong encryption algorithms across all data states
- Least-privilege access: Ensure users and systems can only access minimum information needed for their roles
Identifying "toxic combinations" is particularly important: scenarios where high-sensitivity data sits behind broad or over-permissioned access controls. Modern platforms dynamically map and correlate data sensitivity with access permissions, flagging cases where critical information is accessible to overly broad groups like "Everyone" or "Authenticated Users." By continuously monitoring these relationships and providing remediation guidance, organizations can secure vulnerable data before it's exploited.
Secure and Responsible AI
As organizations rapidly adopt AI technologies, implementing secure and responsible AI practices has become a cornerstone of enterprise data security. AI systems, particularly large language models (LLMs) and generative AI tools, require access to vast amounts of data for training and inference, creating new vectors for data exposure if not properly governed.
The first step is establishing complete visibility into AI deployments. Organizations must discover and inventory all AI copilots and agents operating within their environment, including tools like Microsoft 365 Copilot and Google Gemini, and map exactly which data sources and knowledge bases these systems can access. This visibility is essential because AI tools inherit the permissions of the users who deploy them, meaning that misconfigured access controls can allow AI to surface sensitive information that should remain restricted.
AI Governance Essentials
- Enforce policies that restrict which datasets can be used for AI training or inference
- Track data movement between regions, environments, and into AI pipelines
- Implement role-based access controls specifically designed for AI agents
- Monitor AI-driven interactions continuously and automate remediation when policies are violated
By embedding these controls into AI adoption strategies, enterprises can unlock the productivity benefits of AI while maintaining strict data protection standards.
Continuous Regulatory Compliance
Maintaining continuous regulatory compliance demands an integrated system that embeds compliance into daily operations rather than treating it as a periodic audit exercise. In January 2026, regulatory frameworks are more complex and demanding than ever, with overlapping requirements from GDPR, HIPAA, CCPA, SOC 2, ISO 27001, and the new EU AI Act, among others.
Ongoing monitoring and automation form the backbone of continuous compliance. Systems must continuously scan environments for sensitive data, automatically classify it according to regulatory categories, and generate real-time alerts when compliance violations occur. Automated audit logging captures every access event, configuration change, and data movement, creating an immutable trail of evidence that auditors can review at any time.
Compliance Best Practices
| Practice | Implementation |
|---|---|
| Continuous Monitoring | Real-time scanning and classification of sensitive data with automated alerts |
| Dynamic Access Reviews | Ensure permissions remain aligned with least-privilege principles |
| Policy Updates | Routinely review and update data protection policies to reflect current standards |
| Cross-Department Collaboration | Coordinate between IT, HR, risk management, and engineering teams |
Securing Enterprise Data with Sentra
Sentra is a cloud-native data security platform built for the AI era, delivering AI-ready data governance and compliance by discovering and governing sensitive data at petabyte scale inside your own environment. Instead of copying data into a vendor cloud, Sentra runs scanners in your cloud and on-premises environments, so sensitive content never leaves your control.
Key capabilities: Sentra provides a unified view of sensitive data across IaaS, PaaS, SaaS, data lakes/warehouses, and on‑premises file shares, using AI-powered classification with extremely high accuracy for structured and unstructured data. The platform automatically infers data perimeters (environment, region, account type, etc.) and builds an interactive picture of your data estate, not just where sensitive data lives, but how it moves and changes risk as it travels between clouds, regions, environments, collaboration tools, and AI pipelines.
By correlating data sensitivity, identity, and access controls, Sentra identifies toxic combinations where high‑sensitivity data sits behind broad or over‑permissioned access, including large groups and AI assistants that can traverse permissive ACLs. It continuously monitors permissions, file attributes, and access behavior, then prescribes concrete remediation actions so teams can eliminate risky exposure before it’s exploited. This data‑centric approach is especially critical for AI initiatives: Sentra inventories copilots and agents, maps what they can see, and enforces data‑driven guardrails that control what AI is allowed to do with specific data classes (e.g., no‑summarize / no‑export for highly sensitive content).
Sentra integrates deeply with the Microsoft ecosystem, including Microsoft 365, Purview Information Protection, Azure, and Microsoft 365 Copilot. It automatically classifies and labels sensitive data with high accuracy, then uses those labels to drive policy enforcement via Purview DLP and other downstream controls, ensuring consistent protection across SharePoint, OneDrive, Teams, and broader Microsoft data estates.
Beyond risk reduction, Sentra delivers measurable business value by eliminating shadow data and redundant, obsolete, or trivial (ROT) data, typically cutting cloud storage footprints by around 20% while shrinking the overall data attack surface. Combined with improved compliance readiness and AI‑aware governance, Sentra becomes a strategic platform for enterprises that need to adopt AI securely while maintaining full ownership and control over their most sensitive data.
Conclusion
Enterprise Data Security in 2026 demands a fundamental shift from perimeter-based defenses to data-centric architectures that follow information wherever it moves. Organizations must implement comprehensive strategies that combine automated discovery and classification, proactive threat prevention, continuous compliance monitoring, and secure AI governance. The challenges are significant; data sprawl, toxic permission combinations, unstructured data classification at scale, and the rapid adoption of AI tools all create new attack vectors that traditional security approaches cannot adequately address.
Success requires platforms that provide unified visibility across hybrid environments without compromising data sovereignty, that track data movement in real time to detect risky flows, and that enforce granular access controls aligned with least-privilege principles. By embedding security into every phase of the data lifecycle, from creation and storage to processing and deletion, enterprises can confidently pursue digital transformation and AI innovation while maintaining the trust of customers, partners, and regulators.
<blogcta-big>

BigID Alternatives: 7 Modern DSPM Platforms Compared
BigID Alternatives: 7 Modern DSPM Platforms Compared
Why Teams Look for a BigID Alternative
BigID has become a well‑known name in data privacy, governance, and discovery. But as buyer expectations shift toward security‑first DSPM and cloud data protection, a growing number of teams are actively exploring competitors because they:
- Struggle with slow or brittle scans as environments grow
- Are overwhelmed by noisy data classification, especially on unstructured data
- Need deeper cloud, SaaS, and hybrid coverage than they’re getting today
- Want a platform designed around security operations, not only privacy workflows
- Are squeezed by capacity‑based, enterprise‑heavy pricing and services costs
If that sounds familiar, you’re in the right place. Below are 7 BigID alternatives, plus a simple framework to help you decide which one best fits your use case.
What to Look For in a BigID Alternative
Before we list vendors, it’s worth crystallizing evaluation criteria.
For most organizations rethinking BigID, the right alternative will:
- Deploy with low friction: Agentless or light‑touch integration; days, not quarters, to value.
- Cover your real estate: Cloud, SaaS, and (if relevant) on‑prem file shares/DBs and data lakes.
- Deliver high‑precision classification: Especially for unstructured data and AI/LLM workloads.
- Support security‑led use cases: DSPM, incident response, data detection & response, identity‑aware access governance.
- Offer transparent, scalable economics: Predictable pricing and clear value as you grow.
Keep that lens in mind as you review the options below.
1. Sentra – Best Overall BigID Alternative for Security‑Led DSPM
Best for: Security‑first teams that need a cloud‑native data security platform spanning DSPM, DDR, and data access governance across cloud, SaaS, and hybrid that is highly accurate at discovering and classifying unstructured data at massive scale.
Why teams choose Sentra after BigID
- Security‑built, not privacy‑retrofit: Sentra is designed as a data security platform that unifies:
- Modern coverage: Agentless, in‑environment connections across:
- AWS, Azure, GCP
- Data warehouses and lakes
- SaaS & collaboration (M365, and other key SaaS apps)
- On‑prem file shares and databases
- High‑fidelity classification: AI/NLP‑driven, context‑rich classification to reduce false positives and make findings actionable, particularly on unstructured and AI‑related data.
- Security workflow fit: Risk scoring, exposure dashboards, data-aware alerts, and integrations into SIEM, SOAR, IAM/CIEM, CNAPP, and DLP.
When Sentra is the right BigID alternative
- You’ve hit BigID’s limits around scan performance, noise, or cloud/SaaS depth.
- You’re looking to move from a privacy catalog to a security control plane with measurable risk reduction.
2. Securiti – Strong for Privacy + Data Command Center
Best for: Organizations that want a broad “data command center” for privacy, security, and compliance, and can handle a heavier, platform‑style deployment.
Strengths vs BigID
- Comparable ambition around privacy, governance, and data intelligence, with strong consent and DSAR capabilities.
- Rich feature set and templates aligned to global privacy regulations.
- Good fit where privacy ops and GRC are co‑owners with security.
Tradeoffs
- Can feel heavy and complex to implement and operate, similar to BigID.
- Security‑ops‑oriented DSPM and real‑time detection remain less opinionated than some security‑first platforms.
When to favor Securiti over BigID
- You want a unified privacy + governance hub and are already oriented toward a platform‑style privacy stack.
- You have strong internal resources or partner support for implementation.
3. Cyera – Cloud‑Centric DSPM Peer
Best for: Organizations that want a cloud‑first DSPM with strong discovery across cloud data stores and are largely public‑cloud‑centric.
Strengths vs BigID
- Faster, more cloud‑native deployment than legacy discovery tools.
- Clear positioning around cloud DSPM and risk views.
Tradeoffs
- Emphasis is primarily on cloud data stores; depth for unstructured, SaaS, hybrid, and AI/ML workloads may require close evaluation.
- Less focused on unified DDR and access governance than a full data security platform.
When to favor Cyera over BigID
- You are heavily public‑cloud focused and primarily need DSPM for IaaS/PaaS and data platforms.
- Privacy, DSAR, and governance workflows are secondary to cloud security.
4. Varonis – Legacy DSP for File Systems & On‑Prem
Best for: On‑prem and file‑centric environments, especially where traditional file servers, NAS, and Windows shares remain central.
Strengths vs BigID
- Deep heritage in file‑based data security, permissions analytics, and insider risk in on‑prem Windows/NetApp environments.
- Strong access governance and remediation at the file system layer.
Tradeoffs
- Less natural fit for multi‑cloud and SaaS‑heavy architectures.
- Heavier deployment model; not as cloud‑native or agentless as newer DSPM platforms.
When to favor Varonis over BigID
- Your priority is on‑prem file/system security, and you’re comfortable pairing it with separate tools for cloud DSPM.
- You value mature file/permissions analytics and are not primarily cloud‑native.
5. OneTrust – Privacy, Governance & Trust Platform
Best for: Enterprises that see trust, privacy, ESG, and governance as a unified charter and want a broad platform, with security as one piece of the story.
Strengths vs BigID
- Very broad capabilities across privacy, GRC, ESG, and trust intelligence.
- Flexible configuration for multi‑framework compliance.
Tradeoffs
- Like BigID, OneTrust can be complex and contract‑heavy.
- Security‑led DSPM is not the primary lens; it’s more a component of a larger trust platform.
When to favor OneTrust over BigID
- Your driving force is a privacy + trust office, not the CISO team.
- You want a wide governance platform with DSPM as one of many modules.
6. TrustArc / Osano / Captain Compliance – Lighter Privacy Ops Alternatives
Best for: Organizations primarily shopping for lighter‑weight privacy/compliance tooling like cookie consent, DSAR, RoPA, rather than full DSPM.
Strengths vs BigID
- Simpler, more affordable options for privacy compliance at SMB to upper‑mid‑market scale.
- Faster stand‑up for consent banners, privacy notices, and DSAR workflows.
Tradeoffs
- Not substitutes for enterprise‑grade DSPM or data security platforms.
- Much shallower discovery and risk visibility than BigID, Sentra, or other DSPM tools.
When to favor these tools over BigID
- You’ve realized BigID is overkill for your needs, and your main problem is privacy compliance automation, not comprehensive data security.
- Security teams plan to address DSPM separately.
7. Strac, Wiz, and Other DSPM‑Enabled Security Platforms
There’s a final category of BigID alternatives that matter in some buying cycles:
- Strac: Strong emphasis on SaaS DLP + DSPM for collaboration apps, real‑time remediation, and browser/endpoint controls. Good if your main problem is in‑app DLP for SaaS and GenAI.
- Wiz (with DSPM module): CNAPP platform that added DSPM capabilities. Works best when you want to tie data risk to cloud infrastructure and application risk in one place.
These tools can be good alternatives or complements depending on whether your anchor is application/cloud platform security (CNAPP) or SaaS DLP, rather than a deep data‑first security platform.
How to Decide: A Simple “BigID Alternatives” Decision Guide
Ask yourself three quick questions:
- Who owns the problem?
- Privacy/GRC/legal → consider BigID, Securiti, OneTrust, or lighter privacy tools.
- Security/CISO/cloud security → look hard at Sentra, Cyera, Wiz.
- What’s your environment reality?
- Primarily on‑prem/file shares → Varonis, plus a modern DSPM for cloud.
- Multi‑cloud + SaaS + unstructured + some on‑prem → Sentra stands out.
- Mostly public cloud data platforms → Sentra, Cyera, or Wiz
- What outcome matters most in the next 12–24 months?
- Better privacy governance → BigID, Securiti, OneTrust, TrustArc, Osano, Captain Compliance.
- Fewer data incidents, more security automation, and better AI‑era visibility → Sentra.
Why Sentra Often Ends Up #1 on the Shortlist
Across BigID replacement and augmentation projects, Sentra repeatedly rises to the top because it:
- Treats data security as the core mission, not just discovery or privacy.
- Delivers agentless, in‑environment coverage for cloud, SaaS, and hybrid in one platform.
- Offers high‑fidelity, context‑aware classification to cut noise and focus teams on real risk.
- Unifies DSPM, DDR, and DAG into a single, security‑owned control plane.
If your next move is to replace or supplement BigID with a security‑first platform, Sentra is the logical starting point for your evaluation.
<blogcta-big>

AI Didn’t Create Your Data Risk - It Exposed It
AI Didn’t Create Your Data Risk - It Exposed It
A Practical Maturity Model for AI-Ready Data Security
AI is rapidly reshaping how enterprises create value, but it is also magnifying data risk. Sensitive and regulated data now lives across public clouds, SaaS platforms, collaboration tools, on-prem systems, data lakes, and increasingly, AI copilots and agents.
At the same time, regulatory expectations are rising. Frameworks like GDPR, PCI DSS, HIPAA, SOC 2, ISO 27001, and emerging AI regulations now demand continuous visibility, control, and accountability over where data resides, how it moves, and who - or what - can access it.
Today most organizations cannot confidently answer three foundational questions:
- Where is our sensitive and regulated data?
- How does it move across environments, regions, and AI systems?
- Who (human or AI) can access it, and what are they allowed to do?
This guide presents a three-step maturity model for achieving AI-ready data security using DSPM:
.webp)
- Ensure AI-Ready Compliance through in-environment visibility and data movement analysis
- Extend Governance to enforce least privilege, govern AI behavior, and reduce shadow data
- Automate Remediation with policy-driven controls and integrations
This phased approach enables organizations to reduce risk, support safe AI adoption, and improve operational efficiency, without increasing headcount.
The Convergence of Data, AI, and Regulation
Enterprise data estates have reached unprecedented scale. Organizations routinely manage hundreds of terabytes to petabytes of data across cloud infrastructure, SaaS platforms, analytics systems, and collaboration tools. Each new AI initiative introduces additional data access paths, handlers, and risk surfaces.
At the same time, regulators are raising the bar. Compliance now requires more than static inventories or annual audits. Organizations must demonstrate ongoing control over data residency, access, purpose, and increasingly, AI usage.
Traditional approaches struggle in this environment:
- Infrastructure-centric tools focus on networks and configurations, not data
- Manual classification and static inventories can’t keep pace with dynamic, AI-driven usage
- Siloed tools for privacy, security, and governance create inconsistent views of risk
The result is predictable: over-permissioned access, unmanaged shadow data, AI systems interacting with sensitive information without oversight, and audits that are painful to execute and hard to defend.
Step 1: Ensure AI-Ready Compliance
AI-ready maturity starts with accurate, continuous visibility into sensitive data and how it moves, delivered in a way regulators and internal stakeholders trust.
Outcomes
- A unified view of sensitive and regulated data across cloud, SaaS, on-prem, and AI systems
- High-fidelity classification and labeling, context-enhanced and aligned to regulatory and AI usage requirements
- Continuous insight into how data moves across regions, environments, and AI pipelines
Best Practices
Scan In-Environment
Sensitive data should remain in the organization’s environment. In-environment scanning is easier to defend to privacy teams and regulators while still enabling rich analytics leveraging metadata.
Unify Discovery Across Data Planes
DSPM must cover IaaS, PaaS, data warehouses, collaboration tools, SaaS apps, and emerging AI systems in a single discovery plane.
Prioritize Classification Accuracy
High precision (>95%) is essential. Inaccurate classification undermines automation, AI guardrails, and audit confidence.
Model Data Perimeters and Movement
Go beyond static inventories. Continuously detect when sensitive data crosses boundaries such as regions, environments, or into AI training and inference stores.
What Success Looks Like
Organizations can confidently identify:
- Where sensitive data exists
- Which flows violate policy or regulation
- Which datasets are safe candidates for AI use
Step 2: Extend Governance for People and AI
With visibility in place, organizations must move from knowing to controlling, governing both human and AI access while shrinking the overall data footprint.
Outcomes
- Assign ownership to data
- Least-privilege access at the data level
- Explicit, enforceable AI data usage policies
- Reduced attack surface through shadow and ROT data elimination
Governance Focus Areas
Data-Level Least Privilege
Map users, service accounts, and AI agents to the specific data they access. Use real usage patterns, not just roles, to reduce over-permissioning.
AI-Data Governance
Treat AI systems as high-privilege actors:
- Inventory AI copilots, agents, and knowledge bases
- Use data labels to control what AI can summarize, expose, or export
- Restrict AI access by environment and region
Shadow and ROT Data Reduction
Identify redundant, obsolete, and trivial data using similarity and lineage insights. Align cleanup with retention policies and owners, and track both risk and cost reduction.
What Success Looks Like
- Sensitive data is accessible only to approved identities and AI systems
- AI behavior is governed by enforceable data policies
- The data estate is measurably smaller and better controlled
Step 3: Automate Remediation at Scale
Manual remediation cannot keep up with petabyte-scale environments and continuous AI usage. Mature programs translate policy into automated, auditable action.
Outcomes
- Automated labeling, access control, and masking
- AI guardrails enforced at runtime
- Closed-loop workflows across the security stack
Automation Patterns
Actionable Labeling
Use high-confidence classification to automatically apply and correct sensitivity labels that drive DLP, encryption, retention, and AI usage controls.
Policy-Driven Enforcement
Examples include:
- Auto-restricting access when regulated data appears in an unapproved region
- Blocking AI summarization of highly sensitive or regulated data classes
- Opening tickets and notifying owners automatically
Workflow Integration
Integrate with IAM/CIEM, DLP, ITSM, SIEM/SOAR, and data platforms to ensure findings lead to action, not dashboards.
Benefits
- Faster remediation and lower MTTR
- Reduced storage and infrastructure costs (often ~20%)
- Security teams focus on strategy, not repetitive cleanup
How Sentra and DSPM Can Help
Sentra’s Data Security Platform provides a comprehensive data-centric solution to allow you to achieve best-practice, mature data security. It does so in innovative and unique ways.
Getting Started: A Practical Roadmap
Organizations don’t need a full re-architecture to begin. Successful programs follow a phased approach:
- Establish an AI-Ready Baseline
Connect key environments and identify immediate violations and AI exposure risks. - Pilot Governance in a High-Value Area
Apply least privilege and AI controls to a focused dataset or AI use case. - Introduce Automation Gradually
Start with labeling and alerts, then progress to access revocation and AI blocking as confidence grows. - Measure and Communicate Impact
Track labeling coverage, violations remediated, storage reduction, and AI risks prevented.
In the AI era, data security maturity means more than deploying a DSPM tool. It means:
- Seeing sensitive data and how it moves across environments and AI pipelines
- Governing how both humans and AI interact with that data
- Automating remediation so security teams can keep pace with growth
By following the three-step maturity model - Ensure AI-Ready Compliance, Extend Governance, Automate Remediation - CISOs can reduce risk, enable AI safely, and create measurable economic value.
Are you responsible for securing Enterprise AI? Schedule a demo
<blogcta-big>

Why DSPM Is the Missing Link to Faster Incident Resolution in Data Security
Why DSPM Is the Missing Link to Faster Incident Resolution in Data Security
For CISOs and security leaders responsible for cloud, SaaS, and AI-driven environments, Mean Time to Resolve (MTTR) is one of the most overlooked, and most expensive, metrics in data security.
Every hour a data issue remains unresolved increases the likelihood of a breach, regulatory impact, or reputational damage. Yet MTTR is rarely measured or optimized for data-centric risk, even as sensitive data spreads across environments and fuels AI systems.
Research shows MTTR for data security issues can range from under 24 hours in mature organizations to weeks or months in others. Data Security Posture Management (DSPM) plays a critical role in shrinking MTTR by improving visibility, prioritization, and automation, especially in modern, distributed environments.
MTTR: The Metric That Quietly Drives Data Breach Costs
Whether the issue is publicly exposed PII, over-permissive access to sensitive data, or shadow datasets drifting out of compliance, speed matters. A slow MTTR doesn’t just extend exposure, it expands the blast radius. The longer it takes to resolve an incident the longer sensitive data remains exposed, the more systems, users, and AI tools can interact with it and the more it likely proliferates.
Industry practitioners note that automation and maturity in data security operations are key drivers in reducing MTTR, as contextual risk prioritization and automated remediation workflows dramatically shorten investigation and fix cycles relative to manual methods.
Why Traditional Security Tools Don’t Address Data Exposure MTTR
Most security tools are optimized for infrastructure incidents, not data risk. As a result, security teams are often left answering basic questions manually:
- What data is involved?
- Is it actually sensitive?
- Who owns it?
- How exposed is it?
While teams investigate, the clock keeps ticking.
Example: Cloud Data Exposure MTTR (CSPM-Only)
A publicly exposed cloud storage bucket is flagged by a CSPM tool. It takes hours, sometimes days, to determine whether the data contains regulated PII, whether it’s real or mock data, and who is responsible for fixing it. During that time, the data remains accessible. DSPM changes this dynamic by answering those questions immediately.
How DSPM Directly Reduces Data Exposure MTTR
DSPM isn’t just about knowing where sensitive data lives. In real-world environments, its greatest value is how much faster it helps teams move from detection to resolution. By adding context, prioritization, and automation to data risk, DSPM effectively acts as a response accelerator.
Risk-Based Prioritization
One of the biggest contributors to long MTTR is alert fatigue. Security teams are often overwhelmed with findings, many of which turn out to be false positives or low-impact issues once investigated. DSPM helps cut through that noise by prioritizing risk based on what truly matters: the sensitivity of the data, whether it’s publicly exposed or broadly accessible, who can reach it, and the associated business or regulatory impact.
When combined with cloud security signals like correlating infrastructure exposure identified by CSPM platforms like Wiz with precise data context from DSPM, teams can immediately distinguish between theoretical risk and real sensitive data exposure. These enriched, data-aware findings can then be shared, escalated, or suppressed across the broader security stack, allowing teams to focus their time on fixing the right problems first instead of chasing the loudest alerts.
Faster Investigation Through Built-In Context
Investigation time is another major drag on MTTR. Without DSPM, teams often lose hours or days answering basic questions about an alert: what kind of data is involved, who owns it, where it’s stored, and whether it triggers compliance obligations. DSPM removes much of that friction by precomputing this context. Sensitivity, ownership, access scope, exposure level, and compliance impact are already visible, allowing teams to skip straight to remediation. In mature programs, this alone can reduce investigation time dramatically and prevent issues from lingering simply because no one has enough information to act.
Automation With Validation
One of the strongest MTTR accelerators is closed-loop remediation. Automation plays an equally important role, especially when it’s paired with validation. Instead of relying on manual follow-ups, DSPM can automatically open tickets for critical findings, trigger remediation actions like removing public access or revoking excessive permissions, and then re-scan to confirm the fix actually worked. Issues aren’t closed until validation succeeds. Organizations that adopt this closed-loop model often see critical data risks resolved within hours, and in some cases, minutes - rather than days.
Organizations using this model routinely achieve sub-24-hour MTTR for critical data risks, and in some cases, resolution in minutes.
Removing the End-User Bottleneck
Data issues often stall while waiting for data owners to interpret alerts or determine next steps. DSPM helps eliminate one of the most common bottlenecks in data security: waiting on end users. Data issues frequently stall while teams track down owners, explain alerts, or negotiate next steps. By providing clear, actionable guidance and enabling self-service fixes for common problems, DSPM reduces the need for back-and-forth handoffs. Integrations with ITSM platforms like ServiceNow or Jira ensure accountability without slowing things down. The result is fewer stalled issues and a meaningful reduction in overall MTTR.
Where Do You Stand? MTTR Benchmarks
The DSPM MTTR benchmarks outline clear maturity levels:
| DSPM Maturity | Typical MTTR for Critical Issues |
|---|---|
| Ad-hoc | >72 hours |
| Managed | 48–72 hours |
| Partially Automated | 24–48 hours |
| Advanced Automation | 8–24 hours |
| Optimized | <8 hours |
If your team isn’t tracking MTTR today, you’re likely operating in the top rows of this table, and carrying unnecessary risk.
The Business Case: Faster MTTR = Real ROI
Reducing MTTR is one of the clearest ways to translate data security into business value by achieving:
- Lower breach impact and recovery costs
- Faster containment of exposure
- Reduced analyst burnout and churn
- Stronger compliance posture
Organizations with mature automation detect and contain incidents up to 98 days faster and save millions per incident.
Three Steps to Reduce MTTR With DSPM
- Measure your MTTR for data security findings by severity
- Prioritize data risk, not alert volume
- Automate remediation and validation wherever possible
This shift moves teams from reactive firefighting to proactive data risk management.
MTTR Is the New North Star for Data Security
DSPM is no longer just about visibility. Its real value lies in how quickly organizations can act on what they see.
If your MTTR is measured in days or weeks, risk is already compounding, especially in AI-driven environments.
The organizations that succeed will be those that treat DSPM not as a reporting tool, but as a core engine for faster, smarter response.
Ready to start reducing your data security MTTR? Schedule a Sentra demo.
<blogcta-big>


Securing Sensitive Data in Google Cloud: Sentra Data Security for Modern Cloud and AI Environments
Securing Sensitive Data in Google Cloud: Sentra Data Security for Modern Cloud and AI Environments
As organizations scale their use of Google Cloud, sensitive data is rapidly expanding across cloud storage, data lakes, and analytics platforms, often without clear visibility or consistent control. Native cloud security tools focus on infrastructure and configuration risk, but they do not provide a reliable understanding of what sensitive data actually exists inside cloud environments, or how that data is being accessed and used.
Sentra secures Google Cloud by delivering deep, AI-driven data discovery and classification across cloud-native services, unstructured data stores, and shared environments. With continuous visibility into where sensitive data resides and how exposure evolves over time, security teams can accurately assess real risk, enforce data governance, and reduce the likelihood of data leaks, without slowing cloud adoption.
As data extends into Google Workspace and powers Gemini AI, Sentra ensures sensitive information remains governed and protected across collaboration and AI workflows. When integrated with Cloud Security Posture Management (CSPM) solutions, Sentra enriches cloud posture findings with trusted data context, transforming cloud security signals into prioritized, actionable insight based on actual data exposure.
The Challenge:
Cloud, Collaboration, and AI Without Data Context
Modern enterprises face three converging challenges:
- Massive data sprawl across cloud infrastructure, SaaS collaboration tools, and data lakes
- Unstructured data dominance, representing ~80% of enterprise data and the hardest to classify
- AI systems like Gemini that ingest, transform, and generate sensitive data at scale
While CSPMs, like Wiz, excel at identifying misconfigurations, attack paths, and identity risk, they cannot determine what sensitive data actually exists inside exposed resources. Lightweight or native DSPM signals lack the accuracy and depth required to support confident risk decisions.
Security teams need more than posture - they need data truth.
Data Security Built for the Google Ecosystem
Sentra secures sensitive data across Google Cloud, Google Workspace, and AI-driven environments with accuracy, scale, and control -going beyond visibility to actively reduce data risk.
Key Sentra Capabilities
- AI-Driven Data Discovery & Classification
Precisely identifies PII, PCI, credentials, secrets, IP, and regulated data across structured and unstructured sources—so teams can trust the results. - Best-in-Class Unstructured Data Coverage
Accurately classifies long-form documents and free text, addressing the largest source of enterprise data risk. - Petabyte-Scale, High-Performance Scanning
Fast, efficient scanning designed for cloud and data lake scale without operational disruption. - Unified, Agentless Coverage
Consistent visibility and classification across Google Cloud, Google Workspace, data lakes, SaaS, and on-prem. - Enabling Intelligent Data Loss Prevention (DLP)
Data-aware controls prevent oversharing, public exposure, and misuse—including in AI workflows—driven by accurate classification, not static rules. - Continuous Risk Visibility
Tracks where sensitive data lives and how exposure changes over time, enabling proactive governance and faster response.
Strengthening Security Across Google Cloud & Workspace
Google Cloud
Sentra enhances Google Cloud security by:
- Discovering and classifying sensitive data in GCS, BigQuery, and data lakes
- Identifying overexposed and publicly accessible sensitive data
- Detecting toxic combinations of sensitive data and risky configurations
- Enabling policy-driven governance aligned to compliance and risk tolerance
Google Workspace
Sentra secures the largest source of unstructured data by:
- Classifying sensitive content in Docs, Sheets, Drive, and shared files
- Detecting oversharing and external exposure
- Identifying shadow data created through collaboration
- Supporting audit and compliance with clear reporting
Enabling Secure and Responsible Gemini AI
Gemini AI introduces a new class of data risk. Sensitive information is no longer static, it is continuously ingested and generated by AI systems.
Sentra enables secure and responsible AI adoption by:
- Providing visibility into what sensitive data feeds AI workflows
- Preventing regulated or confidential data from entering AI systems
- Supporting governance policies for responsible AI use
- Reducing the risk of AI-driven data leakage
Wiz + Sentra: Comprehensive Cloud and Data Security
Wiz identifies where cloud risk exists.
Sentra determines what data is actually at risk.
Together, Sentra + Wiz Deliver:
- Enrichment of Wiz findings with accurate, context-rich data classification
- Detection of real exposure, not just theoretical misconfiguration
- Better alert prioritization based on business impact
- Clear, defensible risk reporting for executives and boards
Security teams add Sentra because Wiz alone is not enough to accurately assess data risk at scale, especially for unstructured and AI-driven data.
Business Outcomes
With Sentra securing data across Google Cloud, Google Workspace, and Gemini AI—and enhancing Wiz—organizations achieve:
- Reduced enterprise risk through data-driven prioritization
- Improved compliance readiness beyond minimum regulatory requirements
- Higher SOC efficiency with less noise and faster response
- Confident AI adoption with enforceable governance
- Clearer executive and board-level risk visibility
“Wiz shows us cloud risk. Sentra shows us whether that risk actually impacts sensitive data. Together, they give us confidence to move fast with Google and Gemini without losing control.”
— CISO, Enterprise Organization
As cloud, collaboration, and AI converge, security leaders must go beyond infrastructure-only security. Sentra provides the data intelligence layer that makes Google Cloud security stronger, Google Workspace safer, Gemini AI responsible, and Wiz actionable.
Sentra helps organizations secure what matters most, their critical data.

.webp)
Supercharging DLP with Automatic Data Discovery & Classification of Sensitive Data
Supercharging DLP with Automatic Data Discovery & Classification of Sensitive Data
Data Loss Prevention (DLP) is a keystone of enterprise security, yet traditional DLP solutions continue to suffer from high rates of both false positives and false negatives, primarily because they struggle to accurately identify and classify sensitive data in cloud-first environments.
New advanced data discovery and contextual classification technology directly addresses this gap, transforming DLP from an imprecise, reactive tool into a proactive, highly effective solution for preventing data loss.
Why DLP Solutions Can’t Work Alone
DLP solutions are designed to prevent sensitive or confidential data from leaving your organization, support regulatory compliance, and protect intellectual property and reputation. A noble goal indeed. Yet DLP projects are notoriously anxiety-inducing for CISOs. On the one hand, they often generate a high amount of false positives that disrupt legitimate business activities and further exacerbate alert fatigue for security teams.
What’s worse than false positives? False negatives. Today traditional DLP solutions too often fail to prevent data loss because they cannot efficiently discover and classify sensitive data in dynamic, distributed, and ephemeral cloud environments.
Traditional DLP faces a twofold challenge:
- High False Positives: DLP tools often flag benign or irrelevant data as sensitive, overwhelming security teams with unnecessary alerts and leading to alert fatigue.
- High False Negatives: Sensitive data is frequently missed due to poor or outdated classification, leaving organizations exposed to regulatory, reputational, and operational risks.
These issues stem from DLP’s reliance on basic pattern-matching, static rules, and limited context. As a result, DLP cannot keep pace with the ways organizations use, store, and share data, resulting in the dual-edged sword of both high false positives and false negatives. Furthermore, the explosion of unstructured data types and shadow IT creates blind spots that traditional DLP solutions cannot detect. As a result, DLP often can’t keep pace with the ways organizations use, store, and share data. It isn’t that DLP solutions don’t work, rather they lack the underlying discovery and classification of sensitive data needed to work correctly.
AI-Powered Data Discovery & Classification Layer
Continuous, accurate data classification is the foundation for data security. An AI-powered data discovery and classification platform can act as the intelligence layer that makes DLP work as intended. Here’s how Sentra complements the core limitations of DLP solutions:
1. Continuous, Automated Data Discovery
- Comprehensive Coverage: Discovers sensitive data across all data types and locations - structured and unstructured sources, databases, file shares, code repositories, cloud storage, SaaS platforms, and more.
- Cloud-Native & Agentless: Scans your entire cloud estate (AWS, Azure, GCP, Snowflake, etc.) without agents or data leaving your environment, ensuring privacy and scalability.
- Shadow Data Detection: Uncovers hidden or forgotten (“shadow”) data sets that legacy tools inevitably miss, providing a truly complete data inventory.
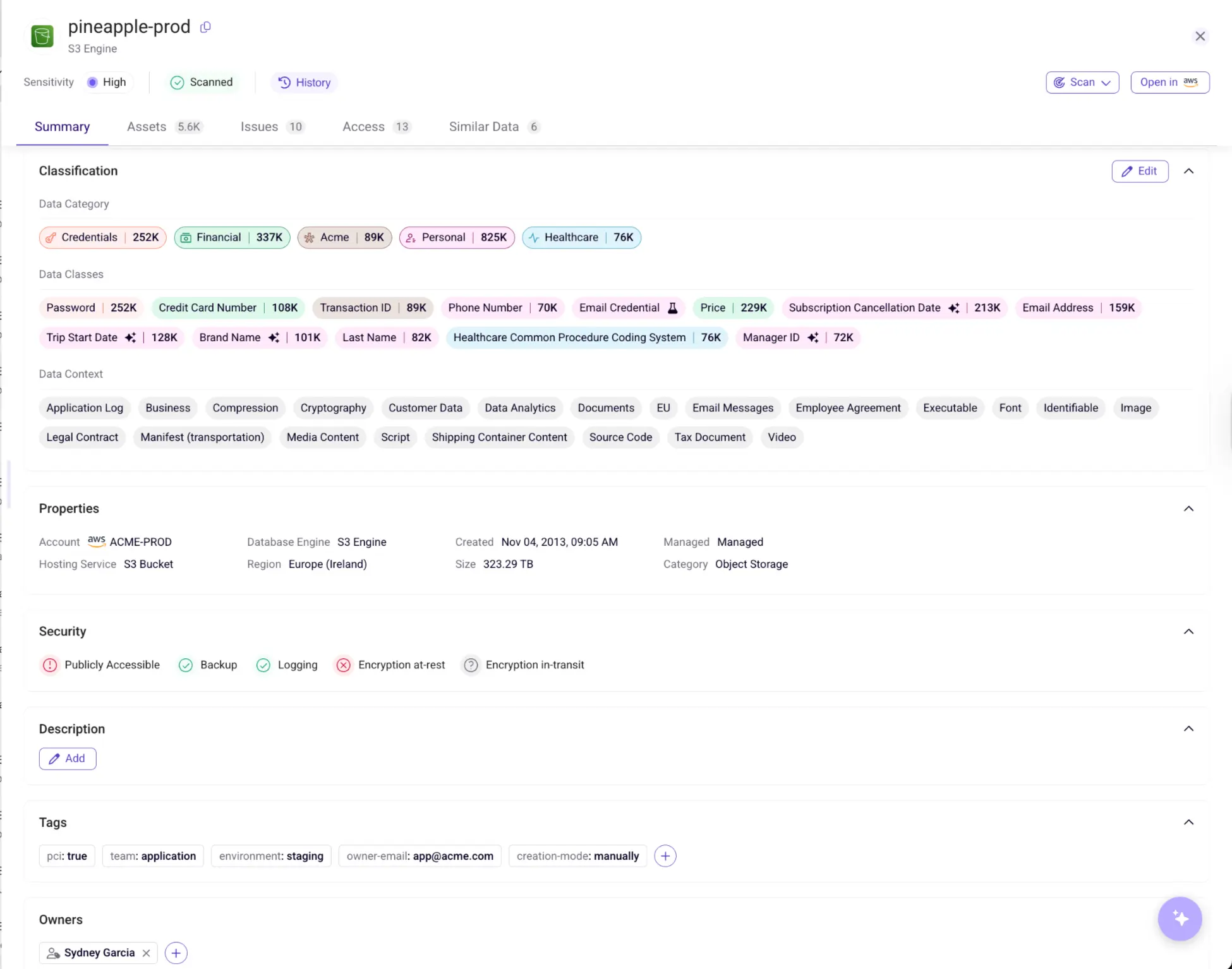
2. Contextual, Accurate Classification
- AI-Driven Precision: Sentra proprietary LLMs and hybrid models achieve over 95% classification accuracy, drastically reducing both false positives and false negatives.
- Contextual Awareness: Sentra goes beyond simple pattern-matching to truly understand business context, data lineage, sensitivity, and usage, ensuring only truly sensitive data is flagged for DLP action.
- Custom Classifiers: Enables organizations to tailor classification to their unique business needs, including proprietary identifiers and nuanced data types, for maximum relevance.
3. Real-Time, Actionable Insights
- Sensitivity Tagging: Automatically tags and labels files with rich metadata, which can be fed directly into your DLP for more granular, context-aware policy enforcement.
- API Integrations: Seamlessly integrates with existing DLP, IR, ITSM, IAM, and compliance tools, enhancing their effectiveness without disrupting existing workflows.
- Continuous Monitoring: Provides ongoing visibility and risk assessment, so your DLP is always working with the latest, most accurate data map.
.webp)
How Sentra Supercharges DLP Solutions

Better Classification Means Less Noise, More Protection
- Reduce Alert Fatigue: Security teams focus on real threats, not chasing false alarms, which results in better resource allocation and faster response times.
- Accelerate Remediation: Context-rich alerts enable faster, more effective incident response, minimizing the window of exposure.
- Regulatory Compliance: Accurate classification supports GDPR, PCI DSS, CCPA, HIPAA, and more, reducing audit risk and ensuring ongoing compliance.
- Protect IP and Reputation: Discover and secure proprietary data, customer information, and business-critical assets, safeguarding your organization’s most valuable resources.
Why Sentra Outperforms Legacy Approaches
Sentra’s hybrid classification framework combines rule-based systems for structured data with advanced LLMs and zero-shot learning for unstructured and novel data types.
This versatility ensures:
- Scalability: Handles petabytes of data across hybrid and multi-cloud environments, adapting as your data landscape evolves.
- Adaptability: Learns and evolves with your business, automatically updating classifications as data and usage patterns change.
- Privacy: All scanning occurs within your environment - no data ever leaves your control, ensuring compliance with even the strictest data residency requirements.
Use Case: Where DLP Alone Fails, Sentra Prevails
A financial services company uses a leading DLP solution to monitor and prevent the unauthorized sharing of sensitive client information, such as account numbers and tax IDs, across cloud storage and email. The DLP is configured with pattern-matching rules and regular expressions for identifying sensitive data.
What Goes Wrong:
An employee uploads a spreadsheet to a shared cloud folder. The spreadsheet contains a mix of client names, account numbers, and internal project notes. However, the account numbers are stored in a non-standard format (e.g., with dashes, spaces, or embedded within other text), and the file is labeled with a generic name like “Q2_Projects.xlsx.” The DLP solution, relying on static patterns and file names, fails to recognize the sensitive data and allows the file to be shared externally. The incident goes undetected until a client reports a data breach.
How Sentra Solves the Problem:
To address this, the security team set out to find a solution capable of discovering and classifying unstructured data without creating more overhead. They selected Sentra for its autonomous ability to continuously discover and classify all types of data across their hybrid cloud environment. Once deployed, Sentra immediately recognizes the context and content of files like the spreadsheet that enabled the data leak. It accurately identifies the embedded account numbers—even in non-standard formats—and tags the file as highly sensitive.
This sensitivity tag is automatically fed into the DLP, which then successfully enforces strict sharing controls and alerts the security team before any external sharing can occur. As a result, all sensitive data is correctly classified and protected, the rate of false negatives was dramatically reduced, and the organization avoids further compliance violations and reputational harm.
Getting Started with Sentra is Easy
- Deploy Agentlessly: No complex installation. Sentra integrates quickly and securely into your environment, minimizing disruption.
- Automate Discovery & Classification: Build a living, accurate inventory of your sensitive data assets, continuously updated as your data landscape changes.
- Enhance DLP Policies: Feed precise, context-rich sensitivity tags into your DLP for smarter, more effective enforcement across all channels.
- Monitor Continuously: Stay ahead of new risks with ongoing discovery, classification, and risk assessment, ensuring your data is always protected.
“Sentra’s contextual classification engine turns DLP from a reactive compliance checkbox into a proactive, business-enabling security platform.”
Fuel DLP with Automatic Discovery & Classification
DLP is an essential data protection tool, but without accurate, context-aware data discovery and classification, it’s incomplete and often ineffective. Sentra supercharges your DLP with continuous data discovery and accurate classification, ensuring you find and protect what matters most—while eliminating noise, inefficiency, and risk.
Ready to see how Sentra can supercharge your DLP? Contact us for a demo today.
<blogcta-big>