The Need for Continuous Compliance
As compliance breaches rise and hefty fines follow, establishing and maintaining strict compliance has become a top priority for enterprises. However, compliance isn't a one-time or even periodic task or something you can set and forget. To stay ahead, organizations are embracing continuous compliance - a proactive, ongoing strategy to meet regulatory requirements and uphold security standards.
Let’s explore what continuous compliance is, the advantages it offers, some challenges it may present, and how Sentra can help organizations achieve and sustain it.
What is Continuous Compliance?
Continuous compliance is the ongoing process of monitoring a company’s security practices and applying appropriate controls to ensure they consistently meet regulatory standards and industry best practices. Instead of treating compliance as a one-time task, it involves real-time monitoring and advanced data protection strategies to catch and address non-compliance issues as they happen. It also includes maintaining a complete inventory of where your data is at all times, what risks and security posture is associated, and who has access to it. This proactive approach, including continuous compliance testing to verify controls are working effectively, ensures you are always ‘audit ready’ and helps avoid last-minute fixes before audits or cyber attacks., ensuring The result is continuous security across the organization.
Why Do Companies Need Continuous Compliance?
Continuous compliance is essential for companies to ensure they are always aligned with industry regulations and standards, reducing the risk of violations and penalties.
Here are a few key reasons why it's crucial:
- Regulatory Changes: Compliance standards frequently evolve. Continuous compliance monitoring ensures companies can adapt quickly to new regulations without major disruptions.
- Avoiding Fines and Penalties: Non-compliance can lead to hefty fines and regulatory enforcement, legal actions or even loss of licenses. Staying compliant helps avoid these risks.
- Protecting Reputation: Data breaches, especially in industries dealing with sensitive data, can damage a company’s reputation. Continuous compliance helps protect established trust with customers, partners, and stakeholders.
- Reducing Security Risks: Many compliance frameworks are designed to enhance data security. Continuous compliance works alongside automated remediation capabilities to keep a company’s security posture is always up-to-date, reducing the risk of data breaches.
- Operational Efficiency: Automated, continuous compliance monitoring can streamline processes, reducing manual audits and interventions, saving time and resources.
For modern businesses, especially those managing sensitive data in the cloud, a continuous cloud compliance strategy is critical to maintaining a secure, efficient, and trusted operation.
Cost Considerations for Compliance Investments
Investing in continuous compliance can lead to significant long-term savings. By maintaining consistent compliance practices, organizations can avoid the hefty fines associated with non-compliance, minimize resource surges during audits, and reduce the impacts of breaches through early detection. Continuous compliance provides security and financial predictability, often resulting in more manageable and predictable expenses.
In contrast, periodic compliance can lead to fluctuating costs. While expenses may be lower between audits, costs typically spike as audit dates approach. These spikes often result from hiring consultants, deploying temporary tools, or incurring overtime charges. Moreover, gaps between audits increase the risk of undetected non-compliance or security breaches, potentially leading to significant unplanned expenses from fines or mitigation efforts.
When evaluating cost implications, it's crucial to look beyond immediate expenses and consider the long-term financial impact. Continuous compliance not only offers a steadier expenditure pattern but also potential savings through proactive measures. On the other hand, periodic compliance can introduce cost variability and financial uncertainties associated with risk management.
Challenges of Continuous Compliance
- Keeping Pace with Technological Advancements: The fast-evolving tech landscape makes compliance a moving target. Organizations need to regularly update their systems to stay in line with new technology, ensuring compliance procedures remain effective. This requires investment in infrastructure that can adapt quickly to these changes. Additionally, keeping up with emerging security risks requires continuous threat detection and response strategies, focusing on real-time compliance monitoring and adaptive security standards to safeguard against new threats.
- Data Privacy and Protection Across Borders: Global organizations face the challenge of navigating multiple, often conflicting, data protection regulations. To maintain compliance, they must implement unified strategies that respect regional differences while adhering to international standards. This includes consistent data sensitivity tagging and secure data storage, transfer, and processing, with measures like encryption and access controls to protect sensitive information.
- Internal Resistance and Cultural Shifts: Implementing continuous compliance often meets internal resistance, requiring effective change management, communication, and education. Building a compliance-oriented culture, where it’s seen as a core value rather than a box-ticking exercise, is crucial.
Organizations must be adaptable, invest in the right technology, and create a culture that embraces compliance. This both helps meet regulatory demands and also strengthens risk management and security resilience.
How You Can Achieve Continuous Compliance With Sentra
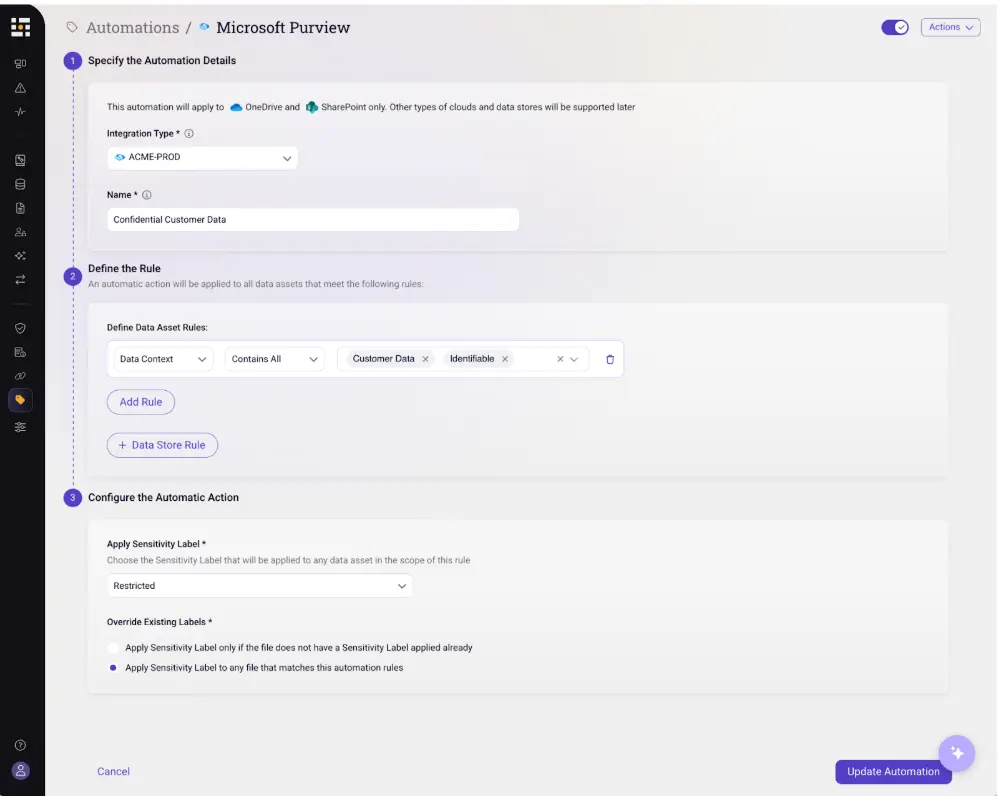
First, Sentra's automated data discovery and classification engine and takes a fraction of the time and effort it would take to manually catalog all sensitive data. It’s far more accurate, especially when using a solution that leverages LLMs to classify data with more granularity and rich context. It’s also more responsive to the frequent changes in your modern data landscape.
Sentra also can automate the process of identifying regulatory violations and ensuring adherence to compliance requirements using pre-built policies that update and evolve with compliance changes (including policies that map to common compliance frameworks). It ensures that sensitive data stays within the correct environments and doesn’t travel to regions in violation of retention policies or without data encryption.

In contrast, manually tracking data inventory is inefficient, difficult to scale, and prone to errors and inaccuracies. This often results in delayed detection of risks, which can require significant time and effort to resolve as compliance audits approach.
<blogcta-big>











.webp)